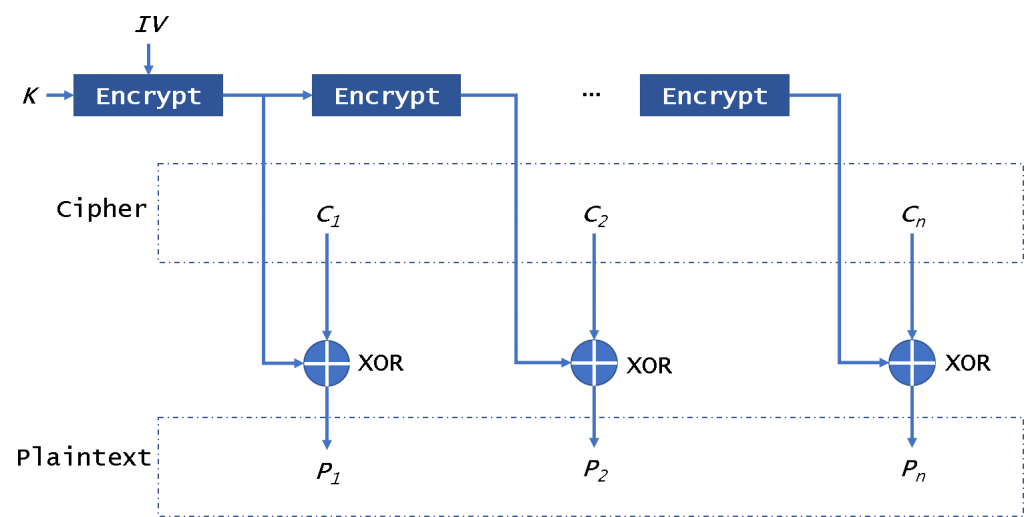
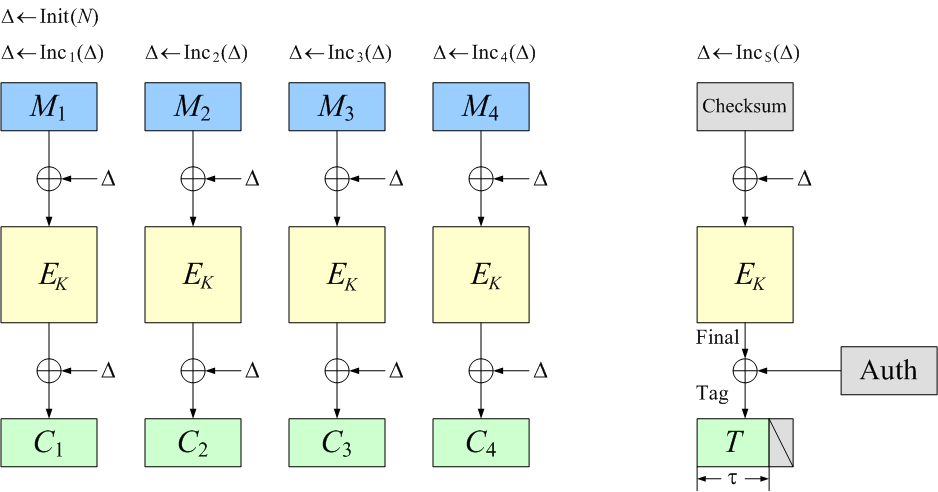
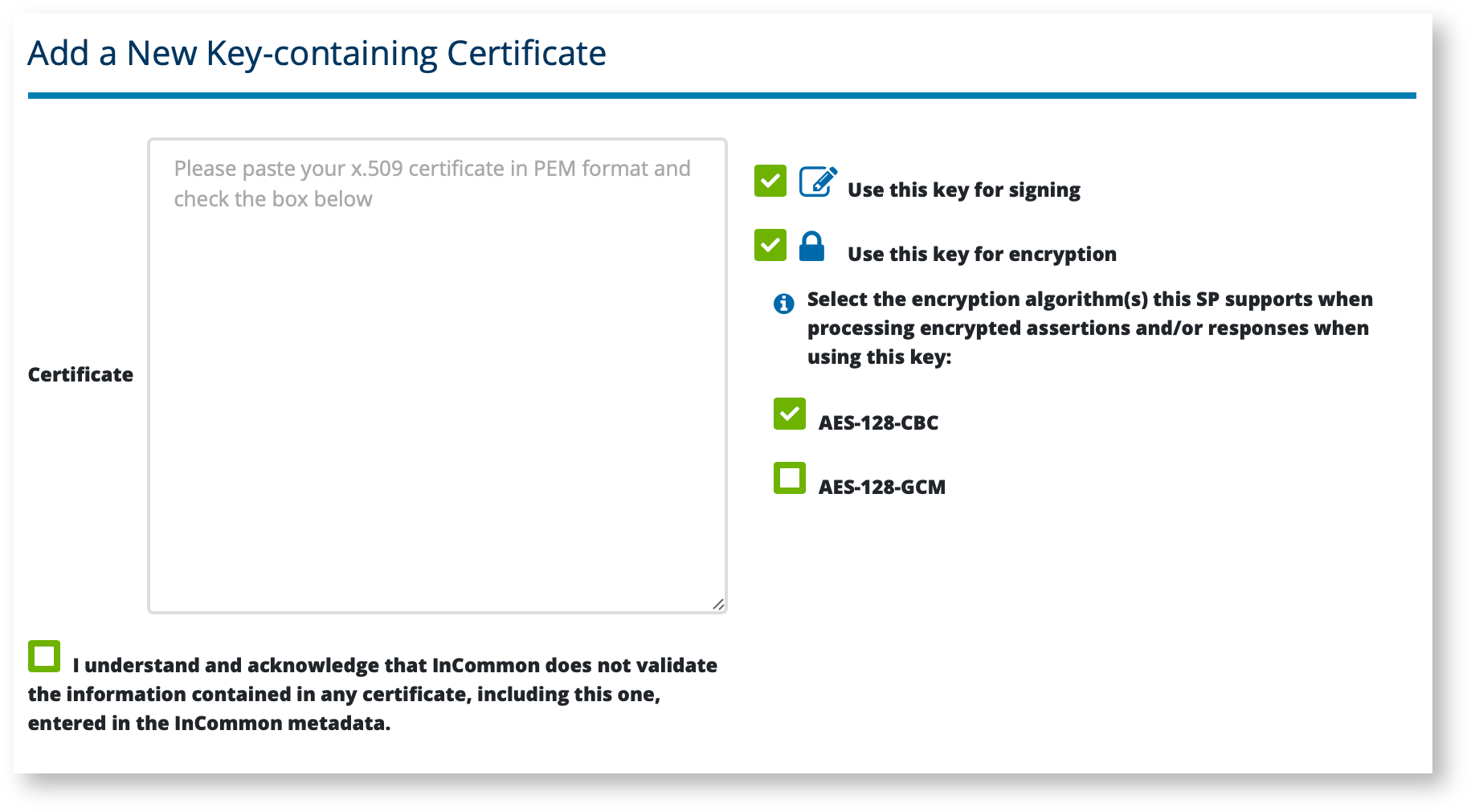
100 Gbit/s AES-GCM Cryptography Engine for Optical Transport Network Systems: Architecture, Design and 40 nm Silicon Prototyping - ScienceDirect

PowerShell - Apply AES-256-GCM decryption on Chrome 91.0.4472.106 cookies stored in the local device - Stack Overflow
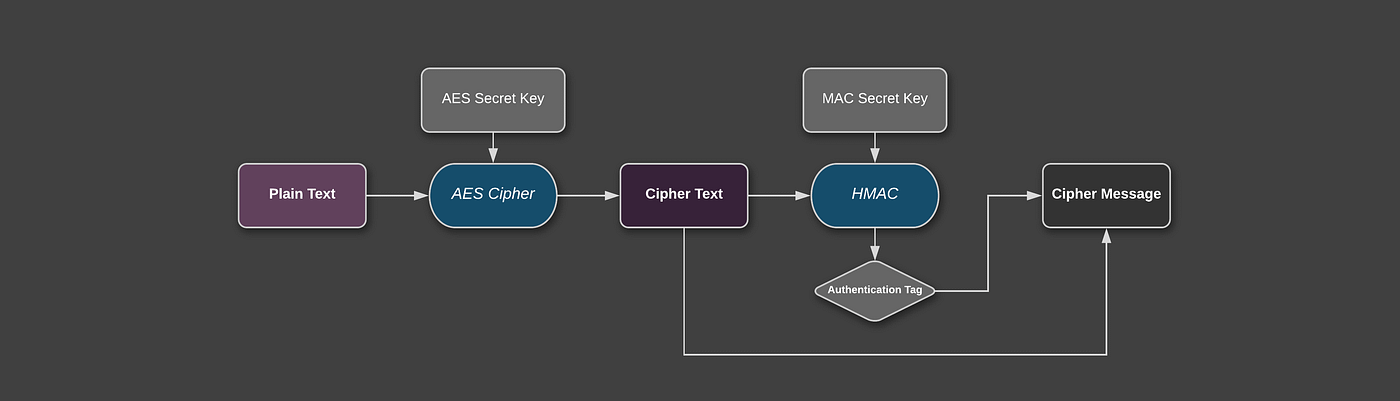
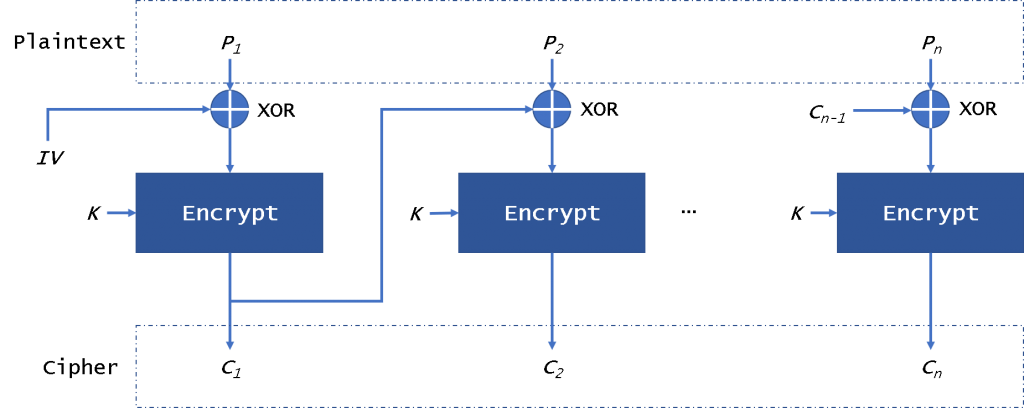
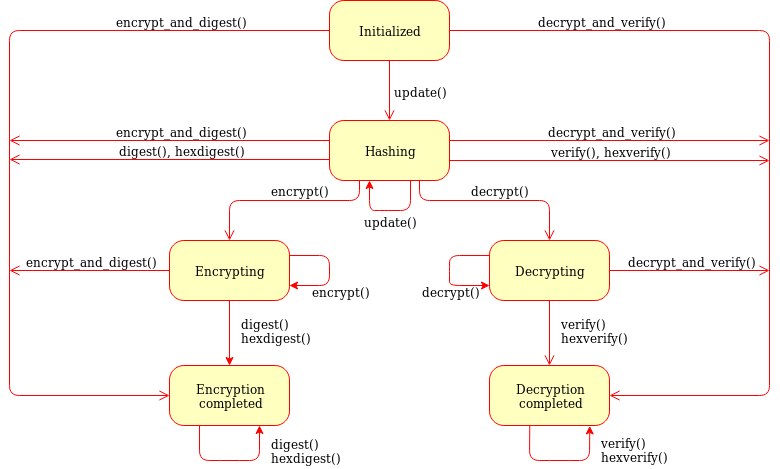
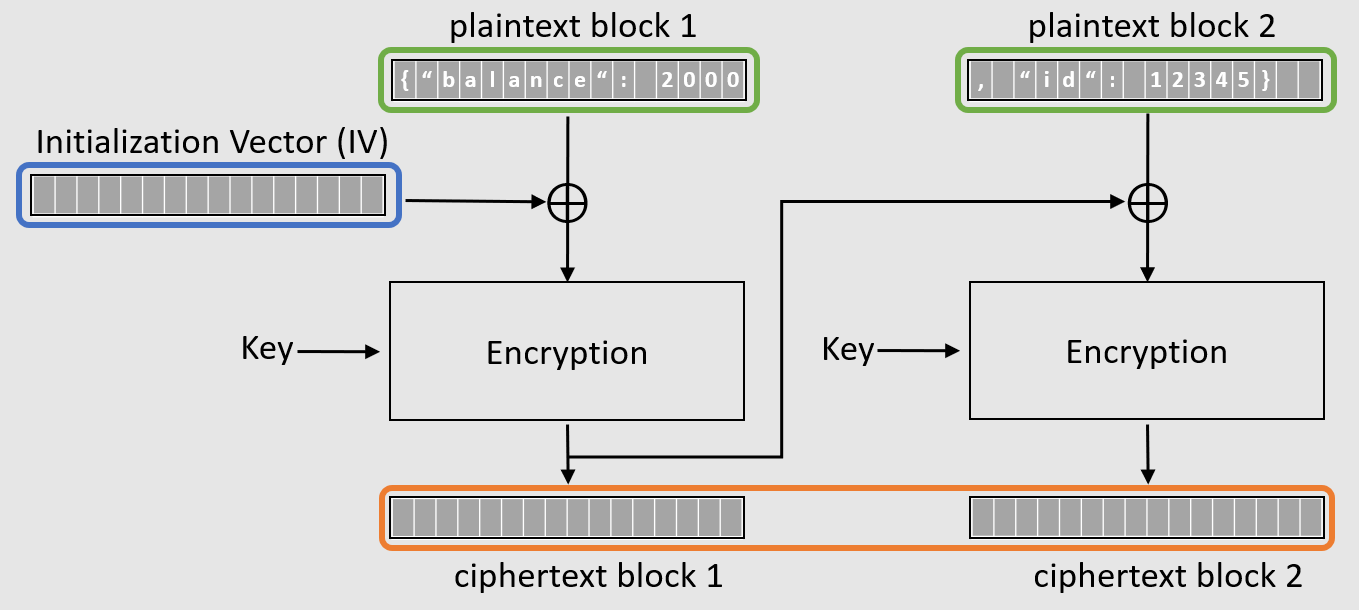
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre-Bulle | ProAndroidDev

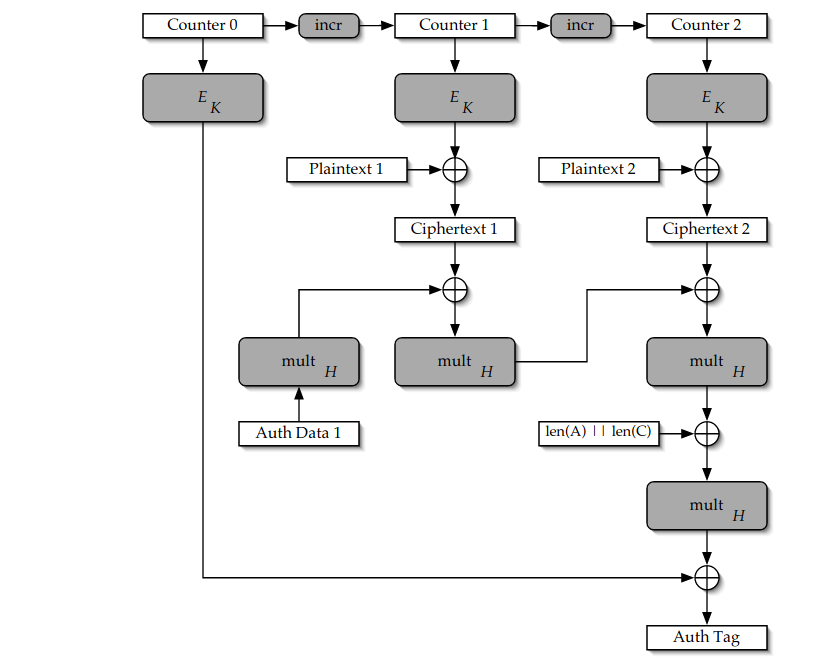
The AES-GCM architecture for an authenticated encryption operation of a... | Download Scientific Diagram