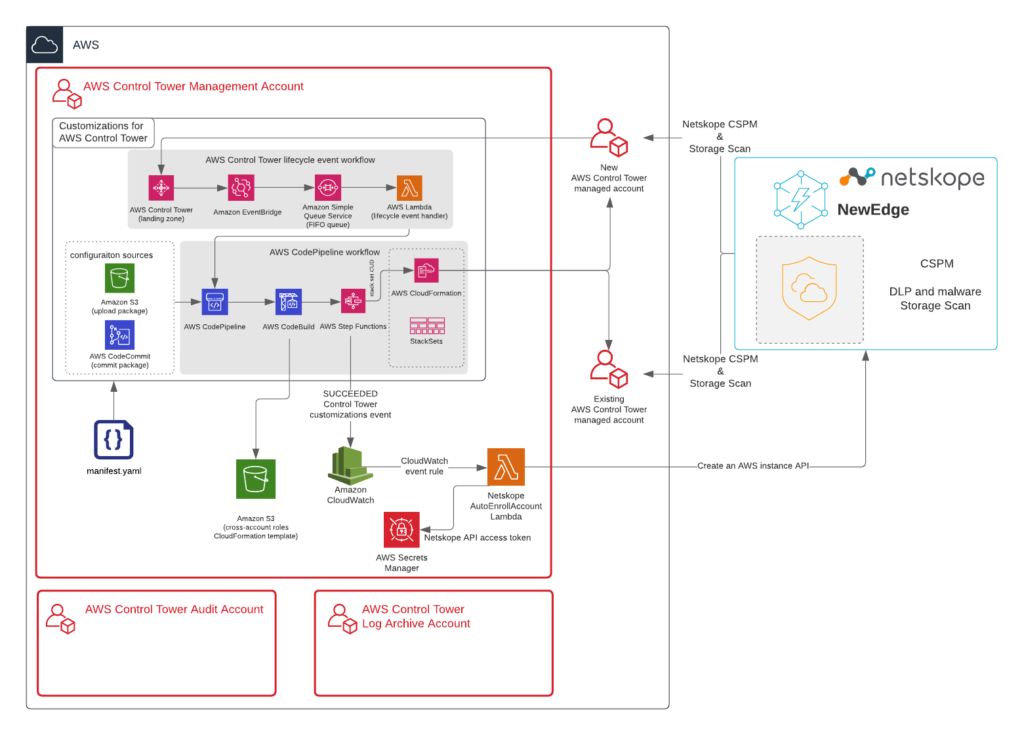
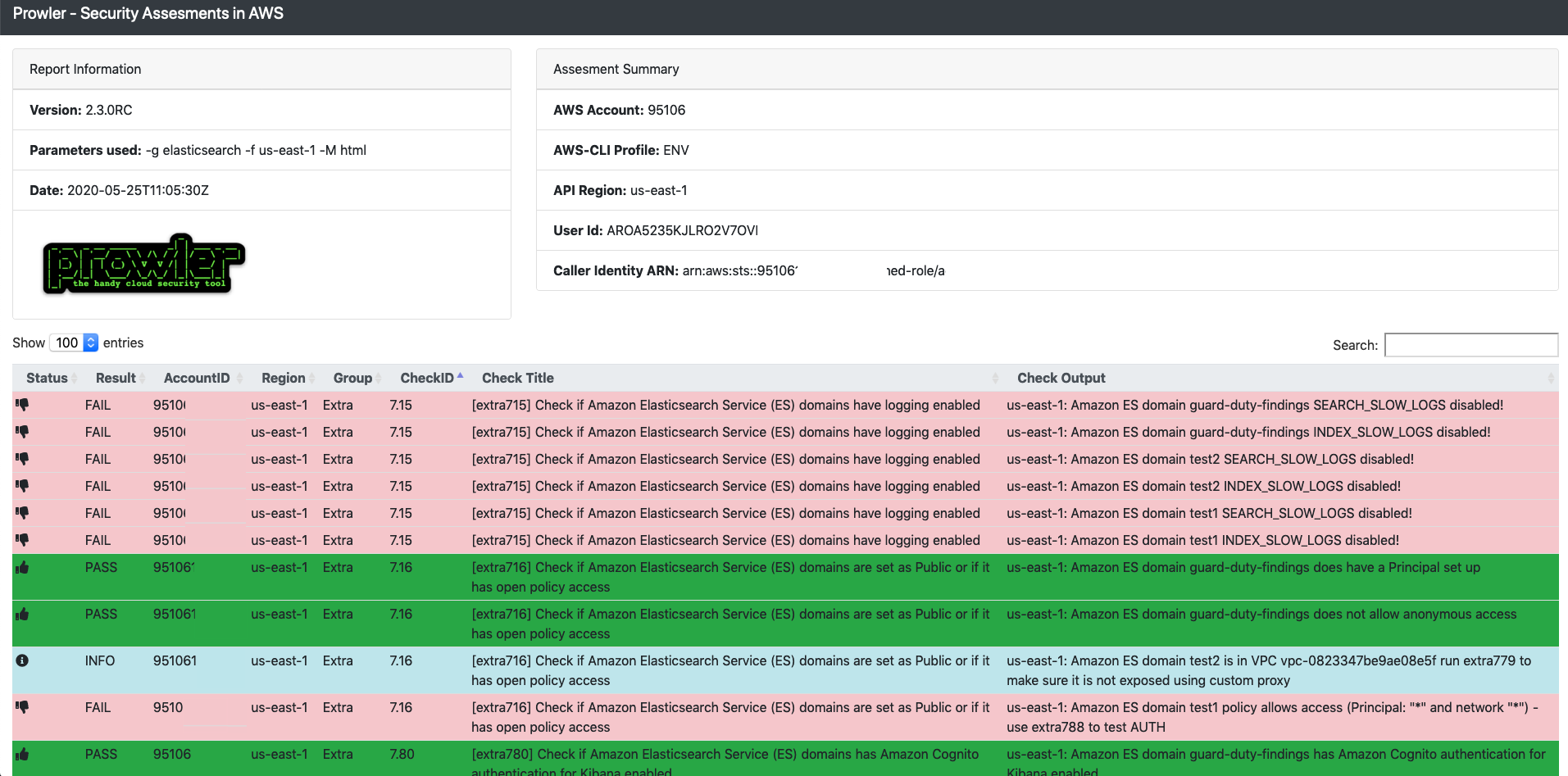
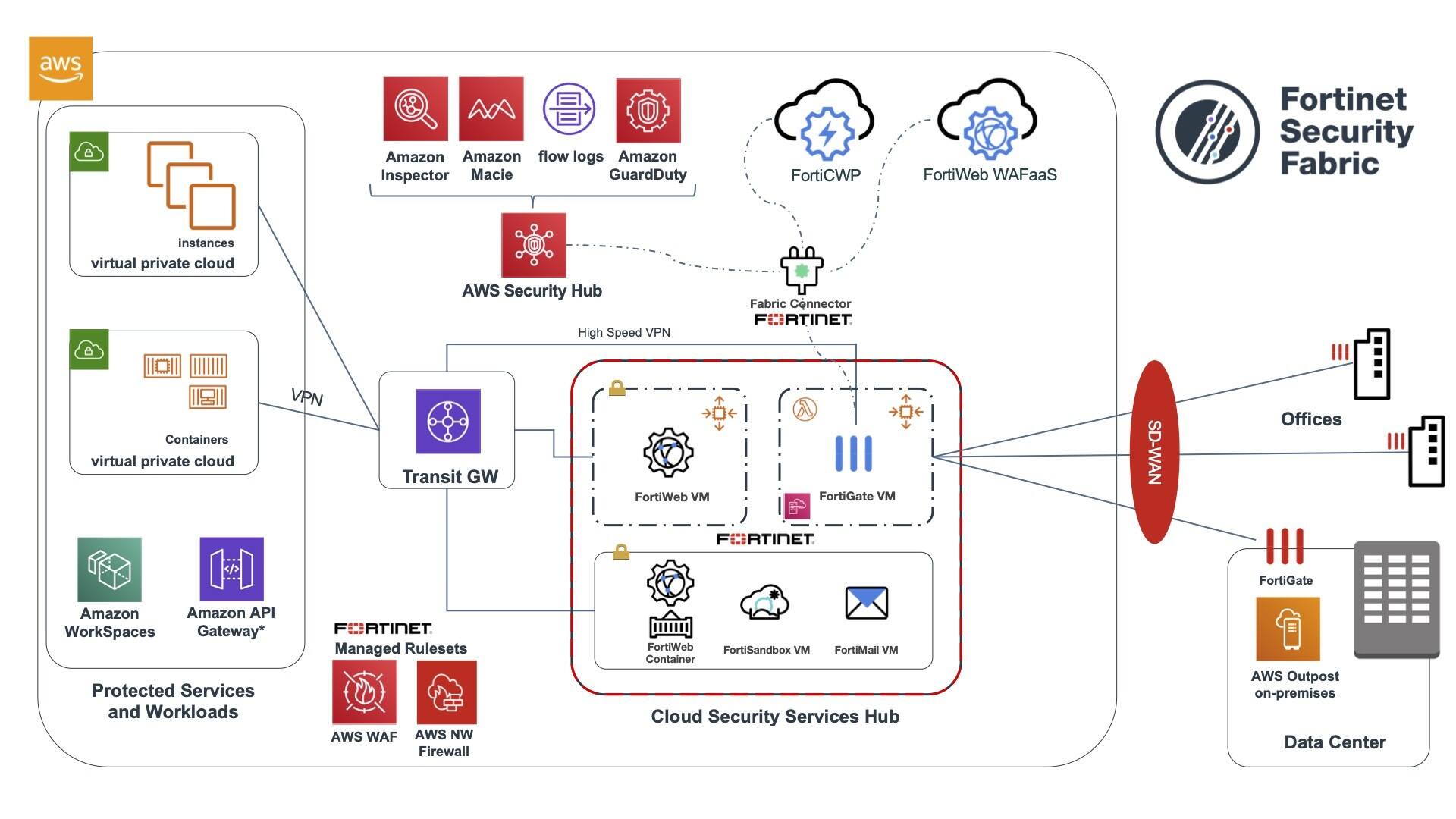
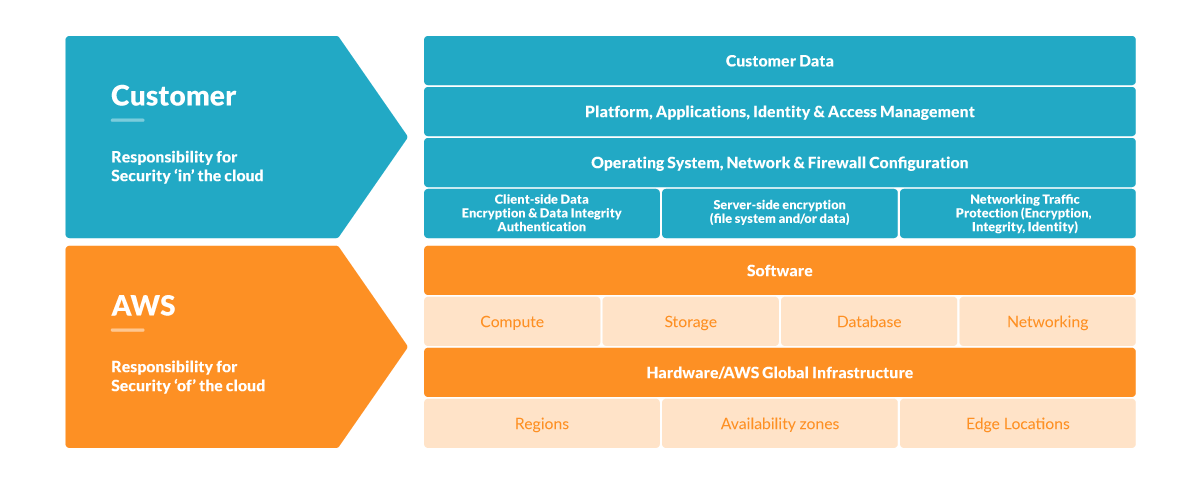
How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

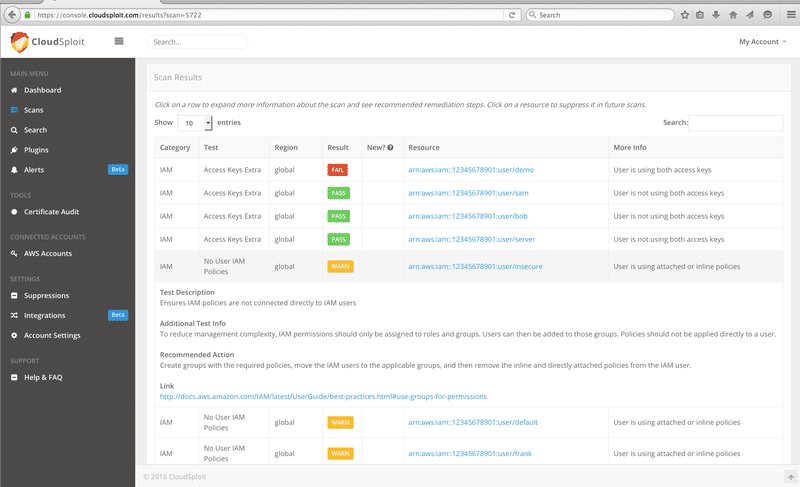
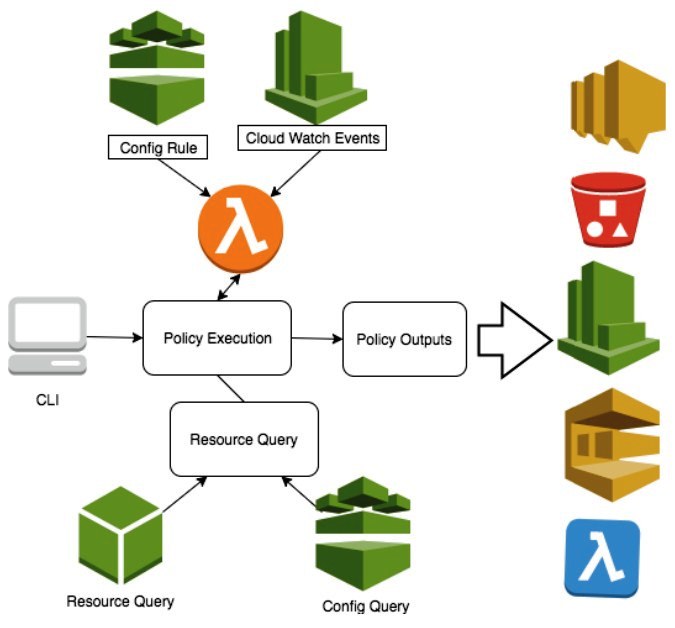
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium

Identifying and resolving security code vulnerabilities using Snyk in AWS CI/CD Pipeline | AWS DevOps Blog

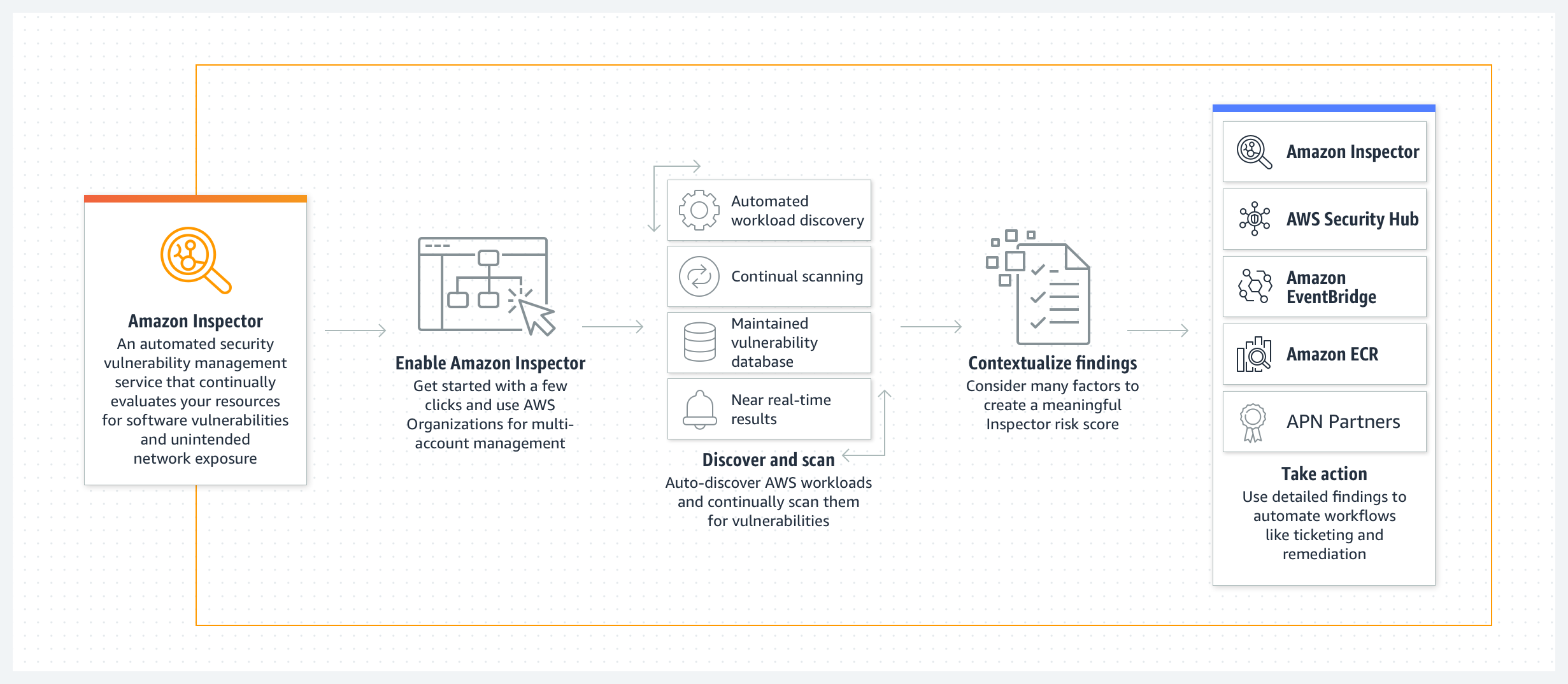
Improved, Automated Vulnerability Management for Cloud Workloads with a New Amazon Inspector | AWS News Blog
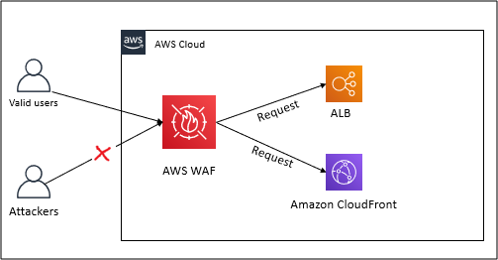
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium