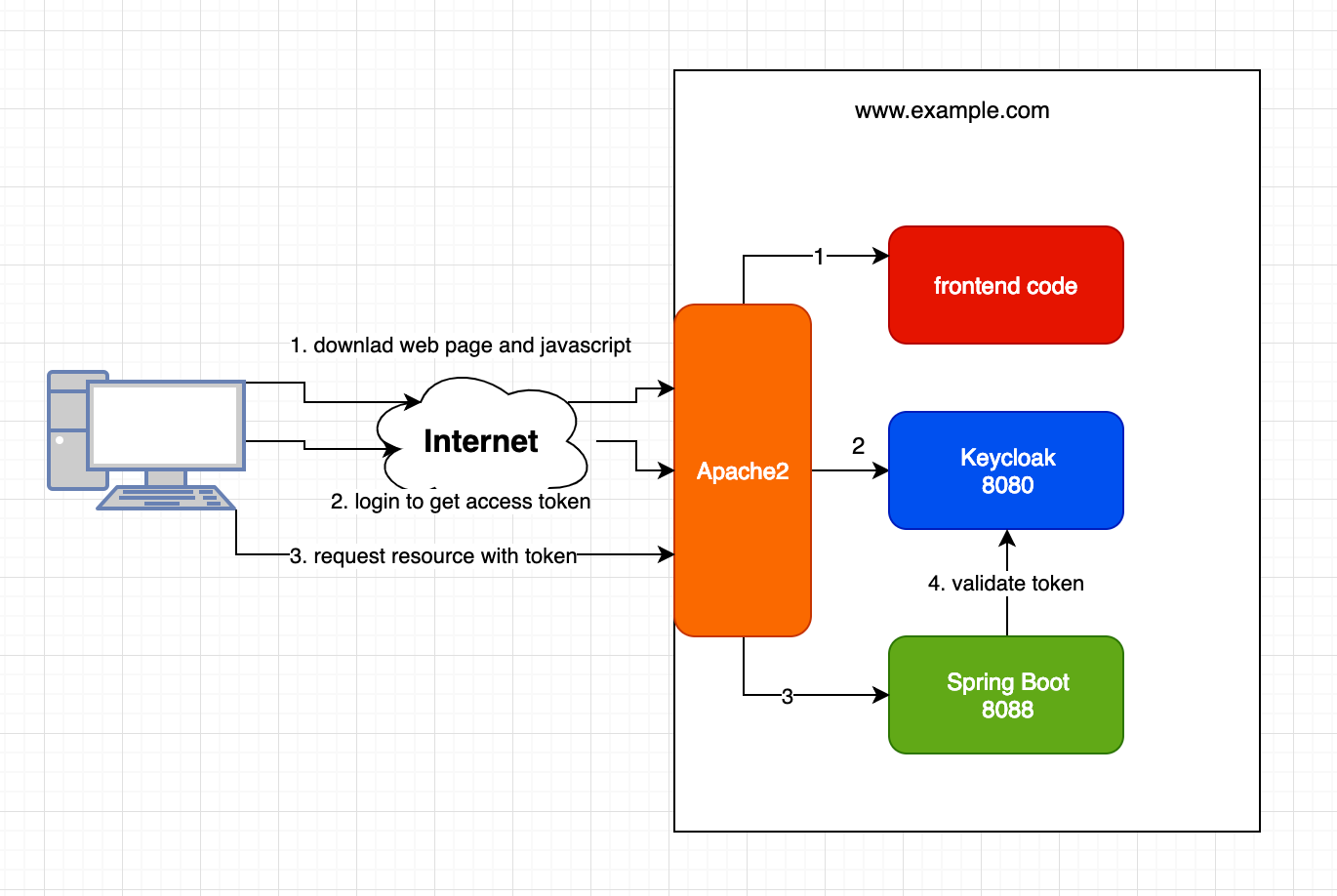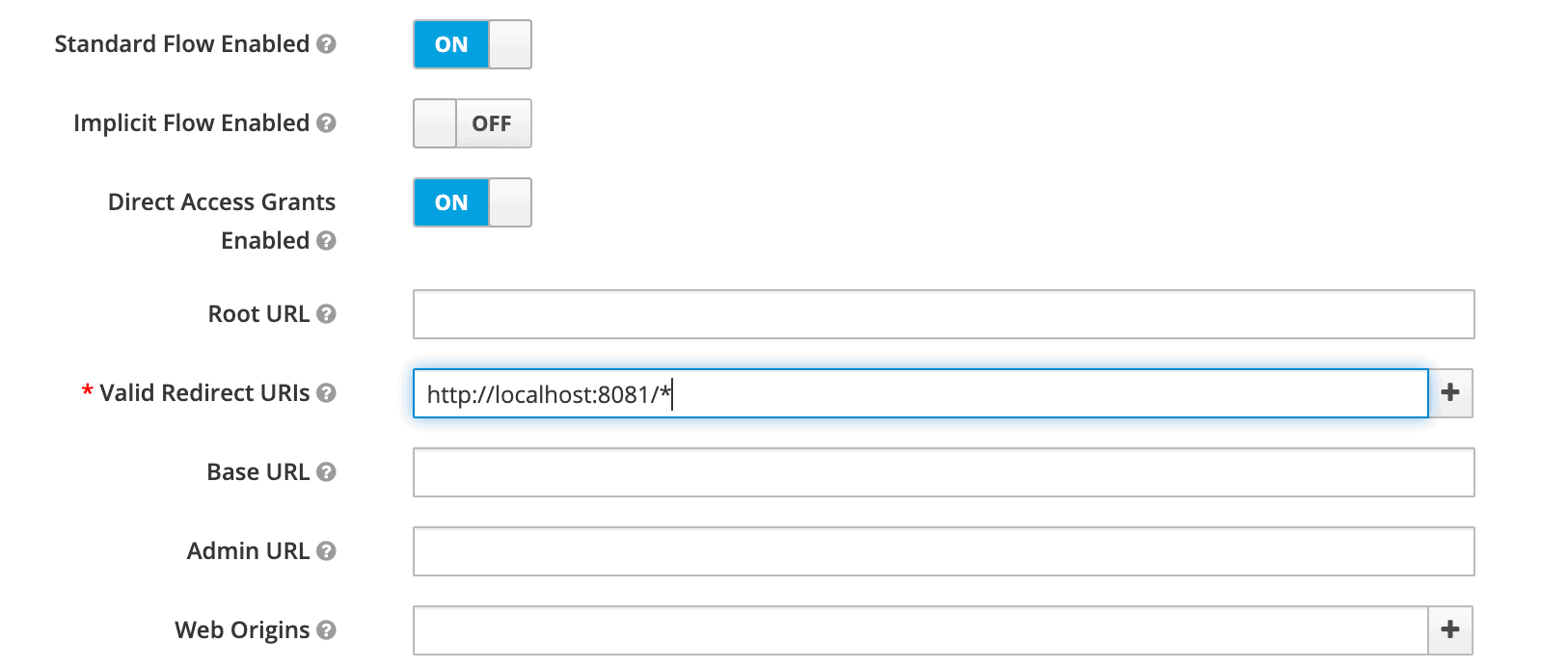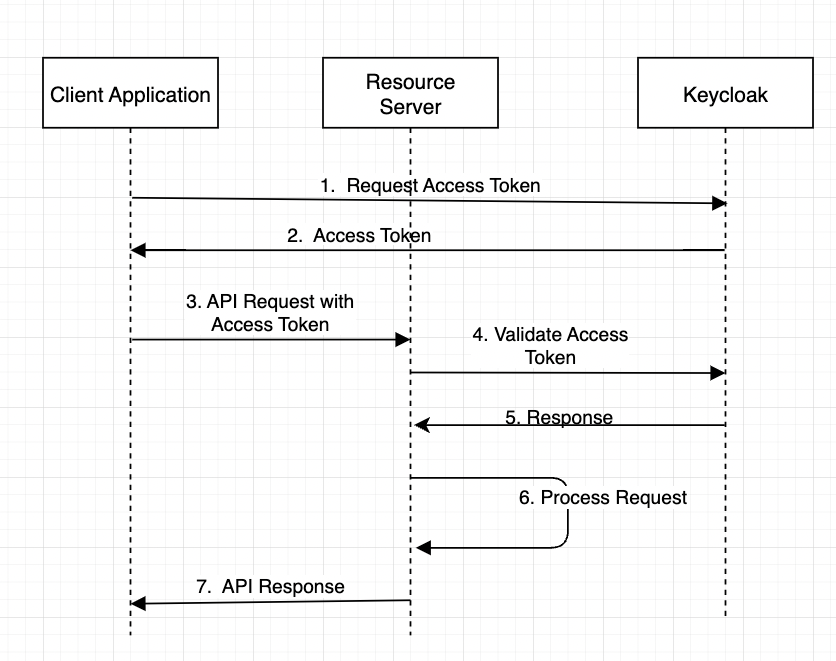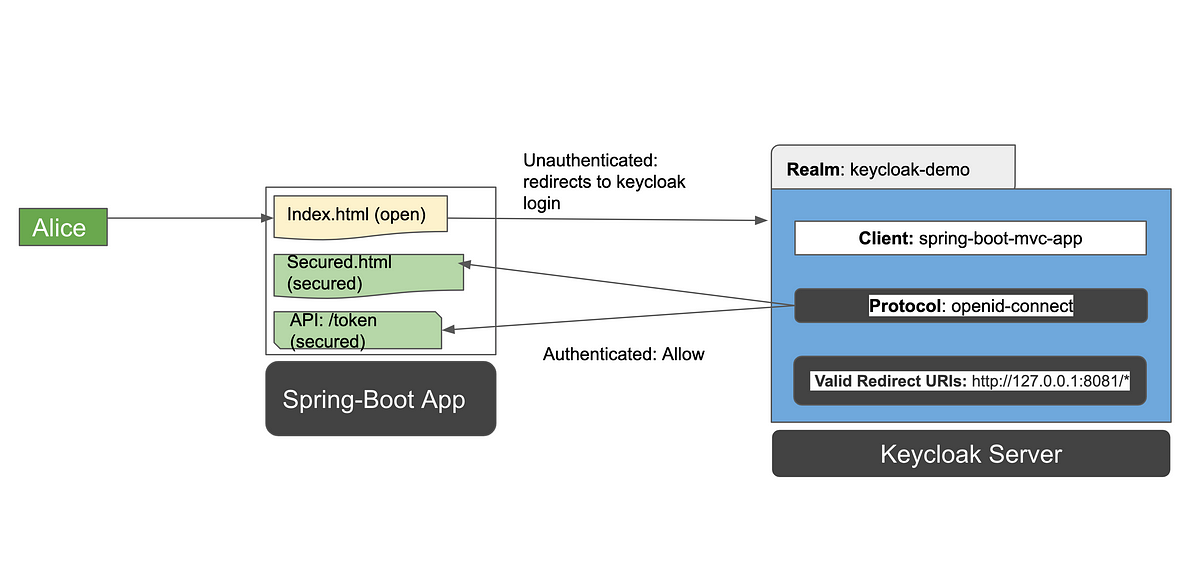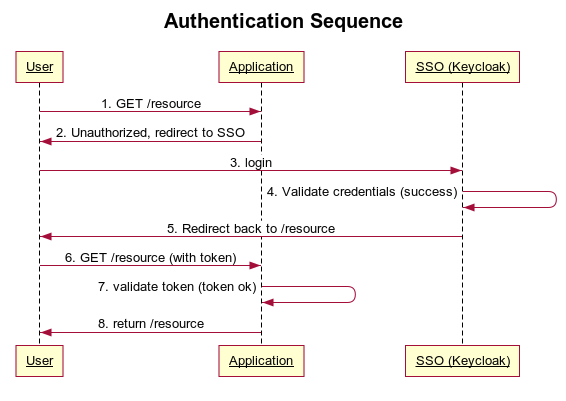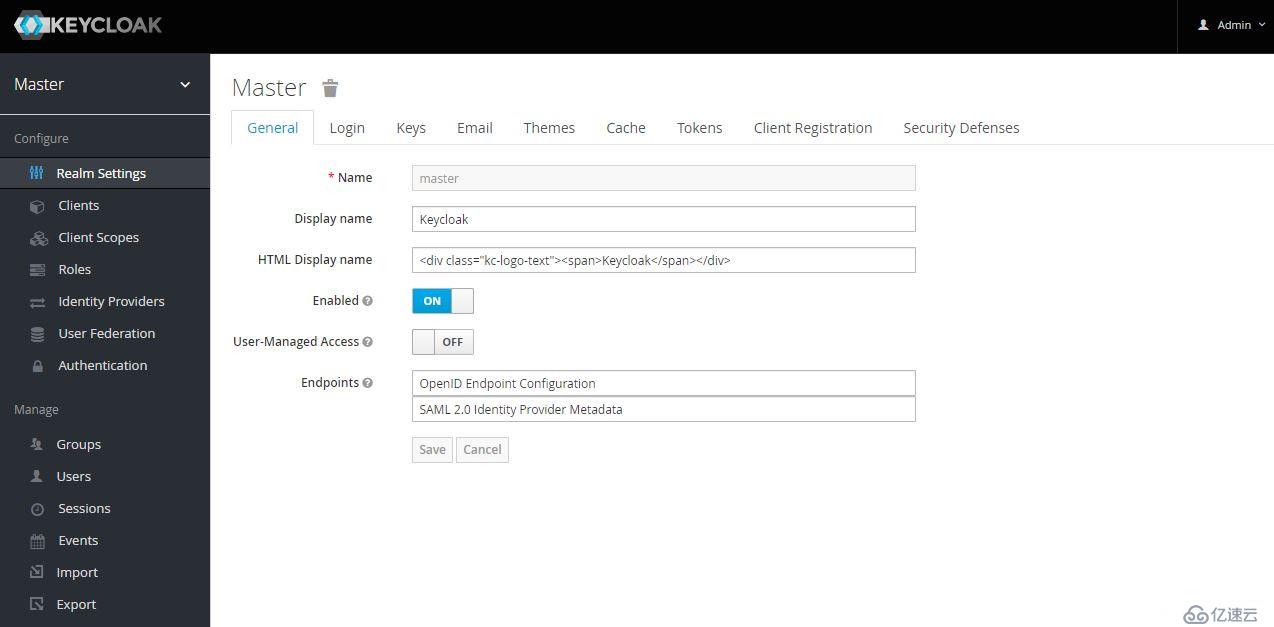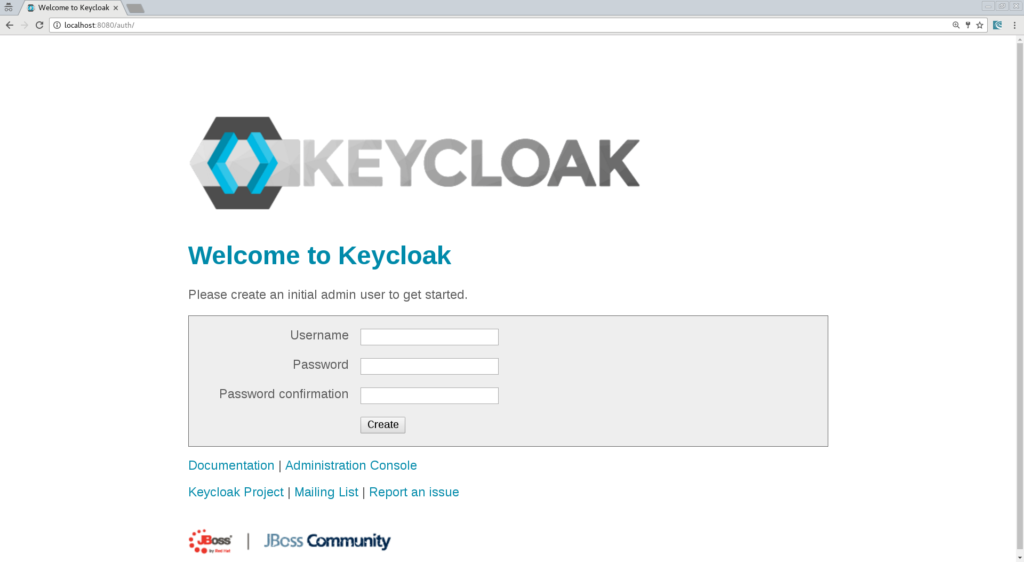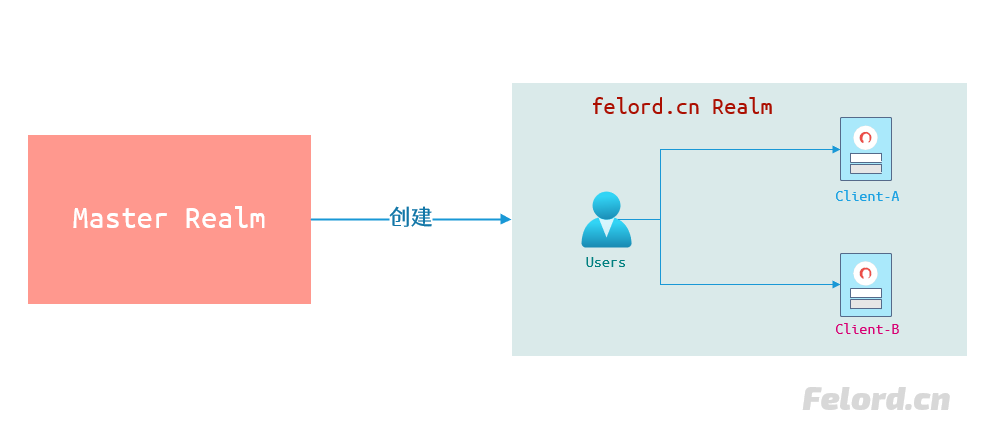
Protecting Your Spring Boot Applications with the Keycloak Authentication Authorization Platform - Spring Cloud
keycloak 15.0.2] [Adapter] - [Spring.Boot 2.6] - Application don't start because of Circular Reference due to dependency injection · Issue #8857 · keycloak/keycloak · GitHub
GitHub - thomasdarimont/spring-boot-2-keycloak-oauth-example: PoC for Spring Boot 2 + Spring Security 5 + Keycloak 3.4.3 without Keycloak Adapter

Keyloak quick start guide. It only takes 10 minutes to access spring boot / Vue front-end and back-end separate applications to realize SSO single sign on | Develop Paper
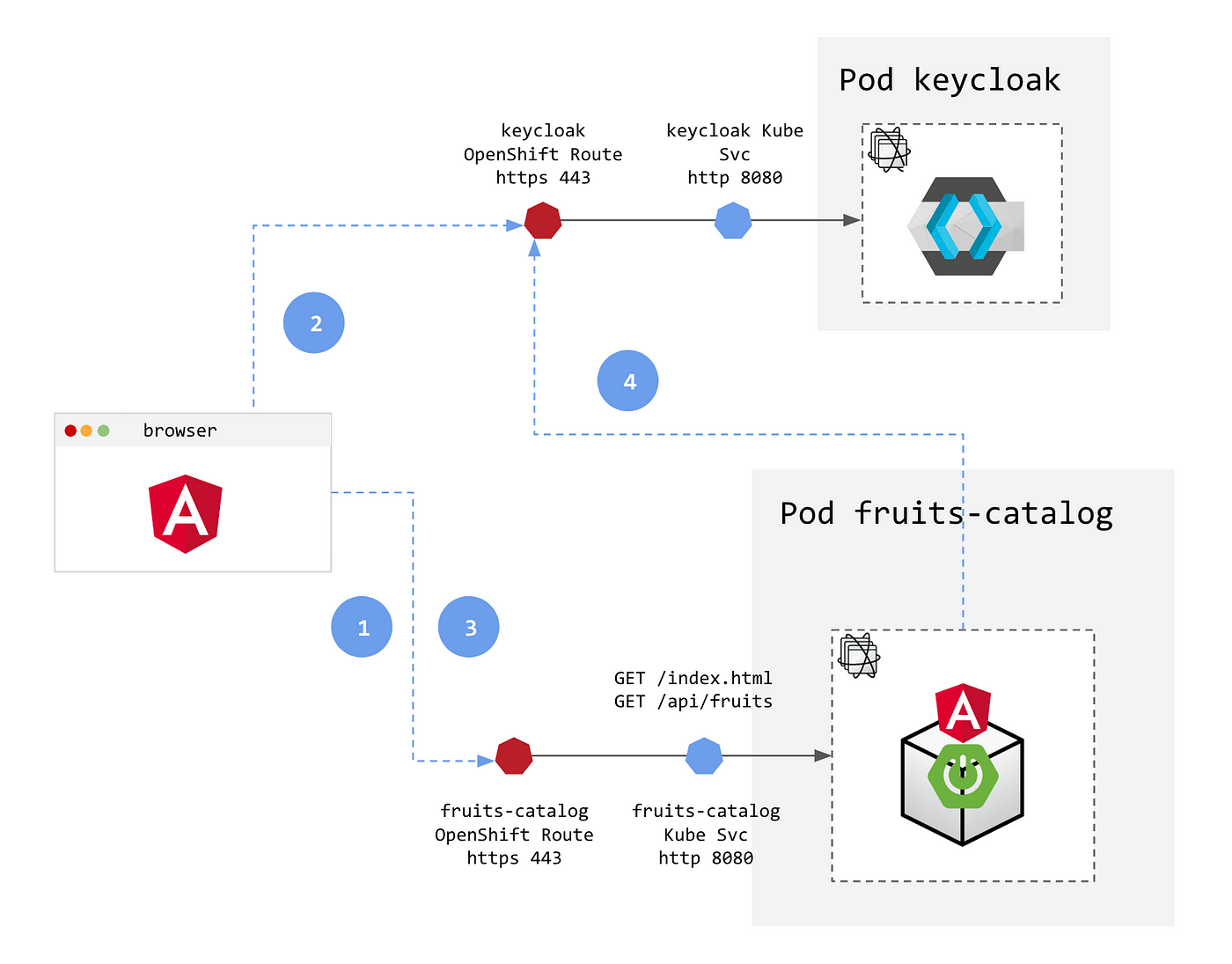
Adding security layers to your App on OpenShift — Part 2: Authentication and Authorization with Keycloak | by Laurent Broudoux | ITNEXT