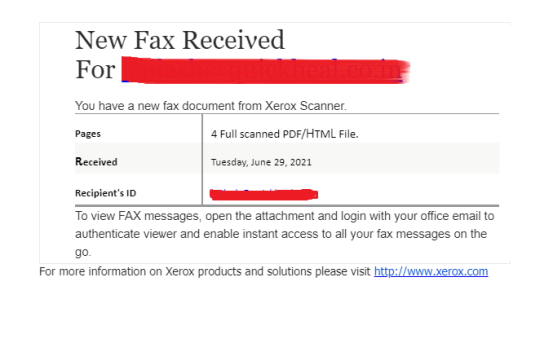
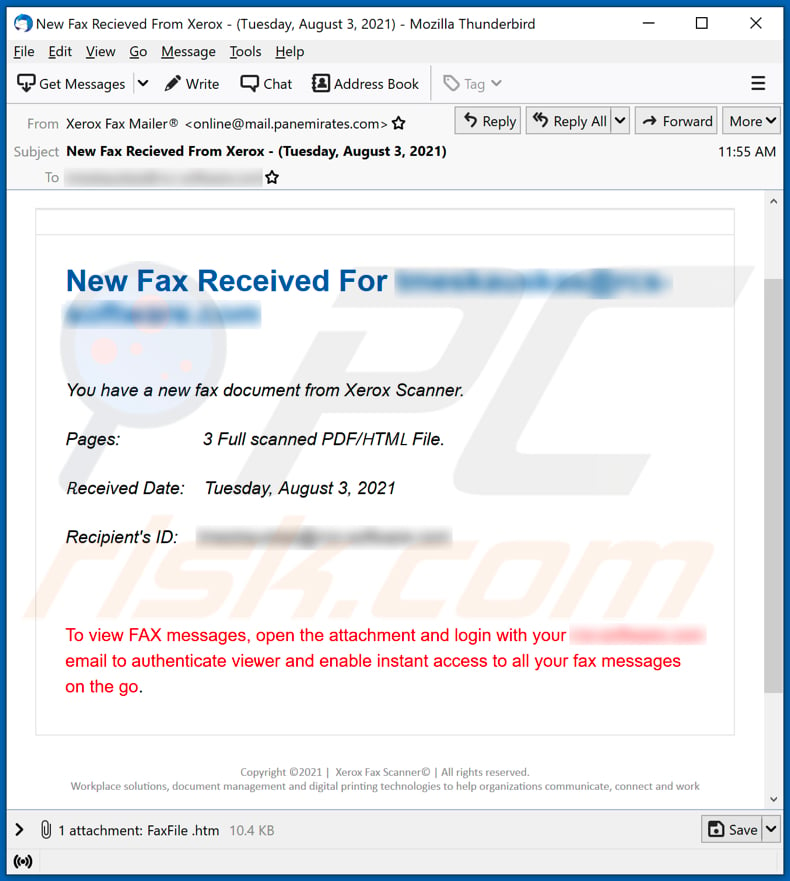
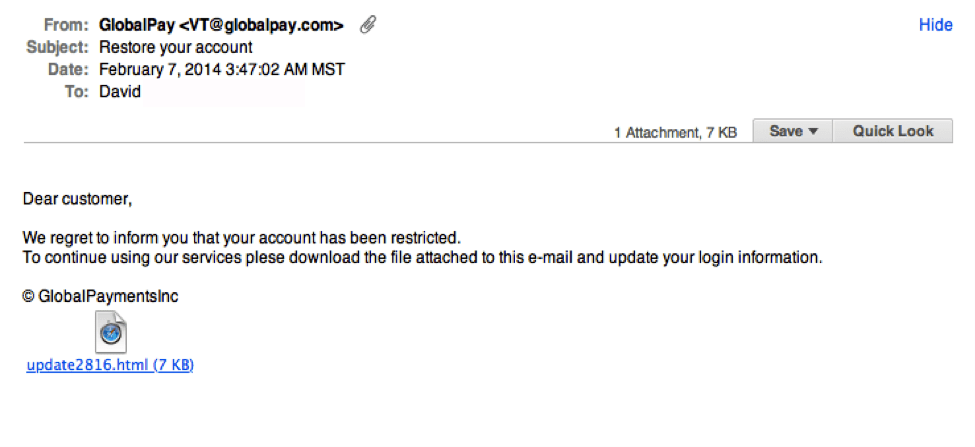
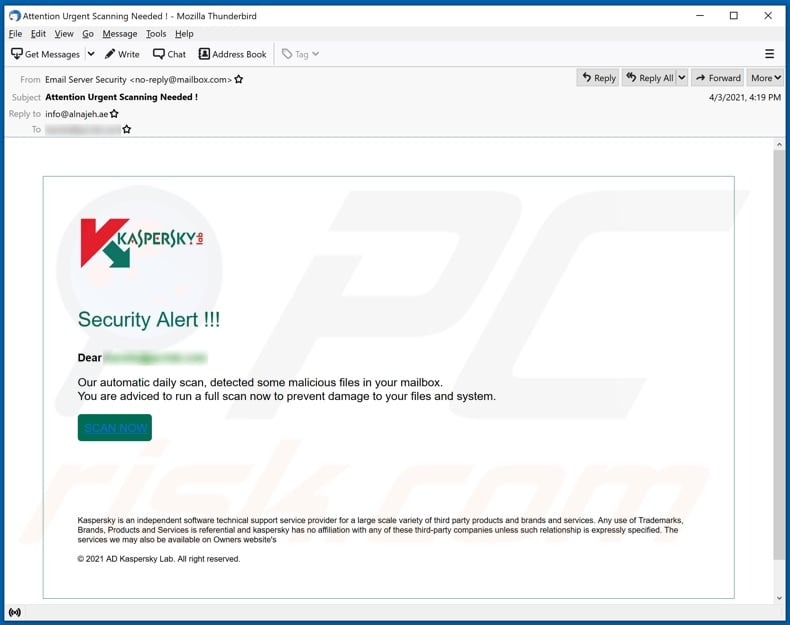
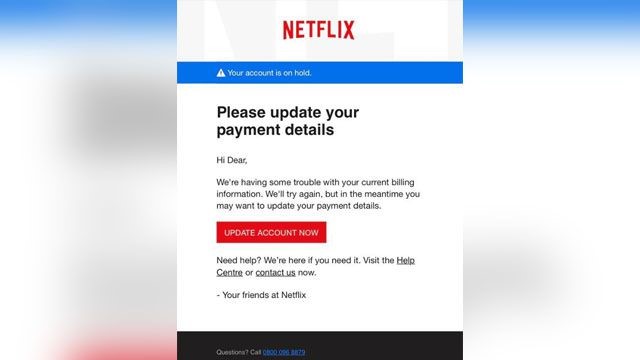
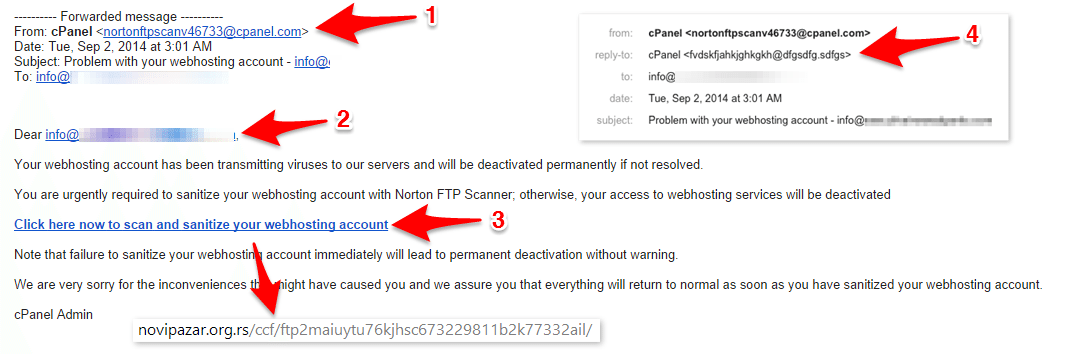
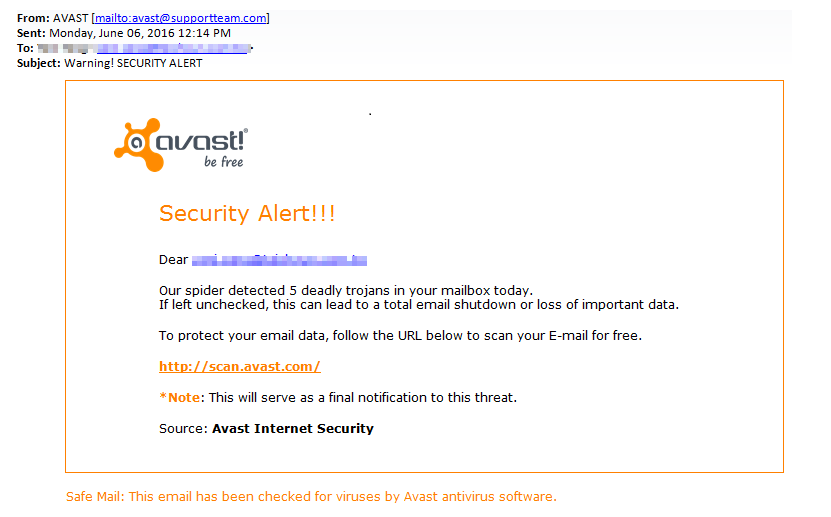
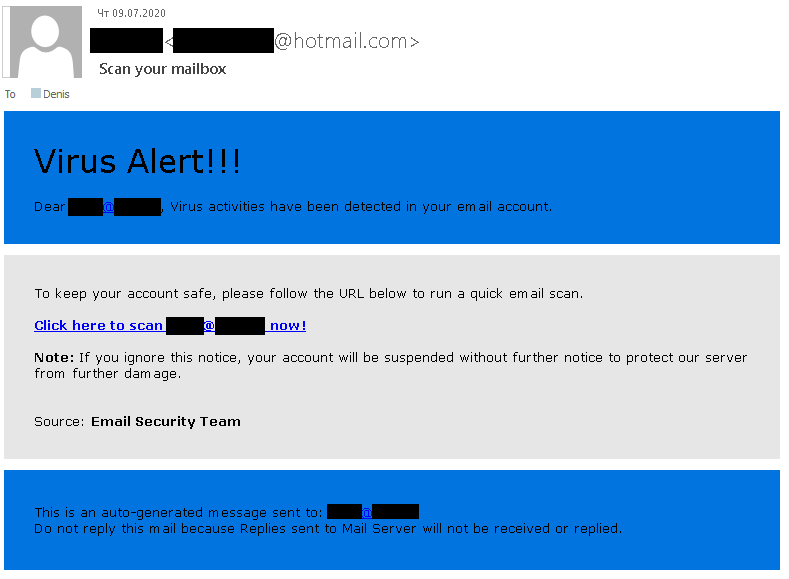
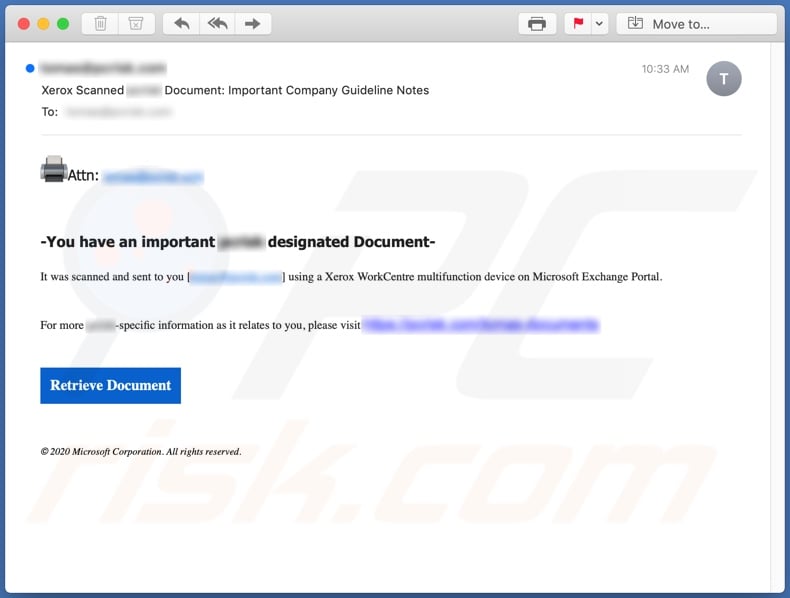
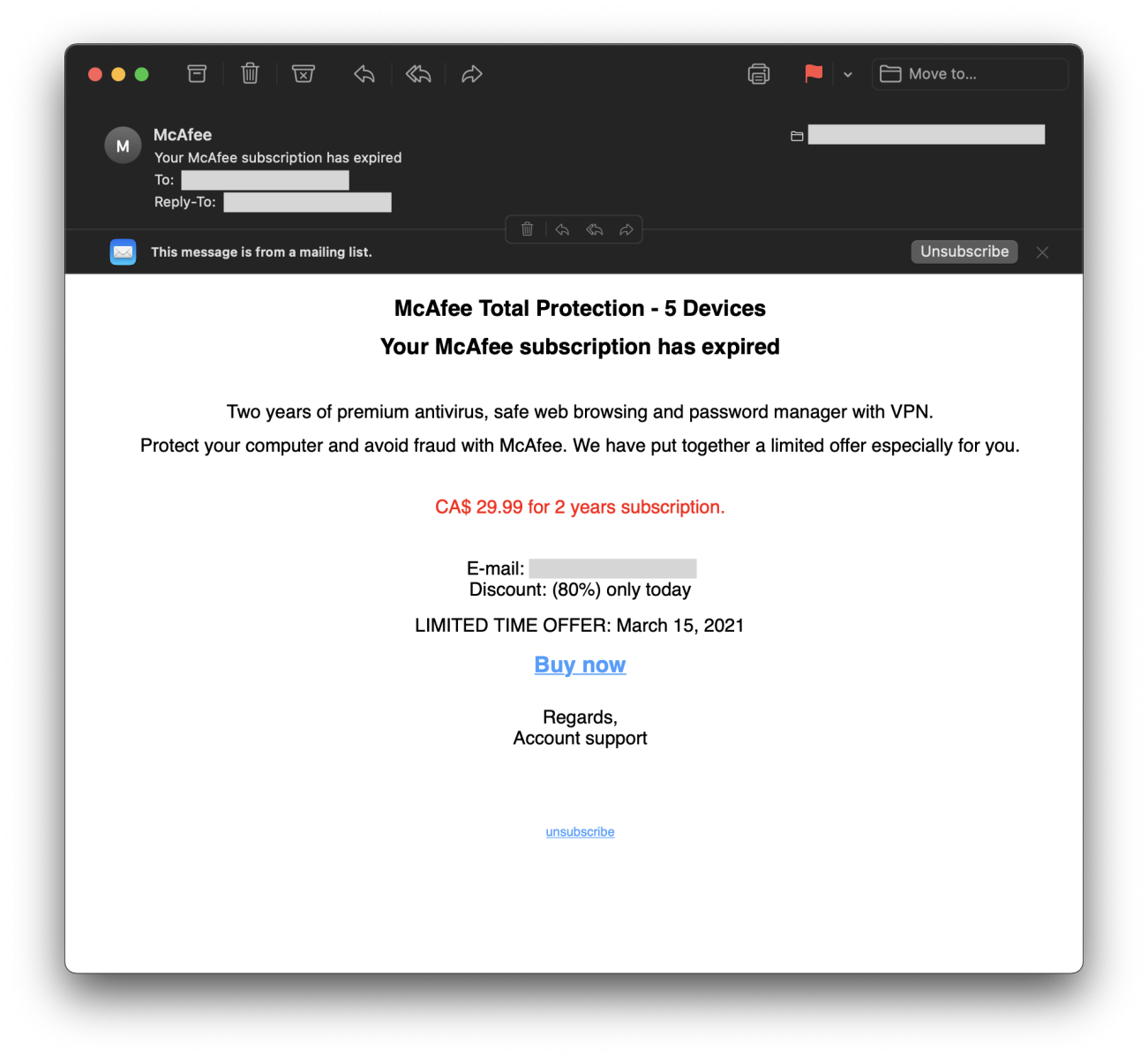
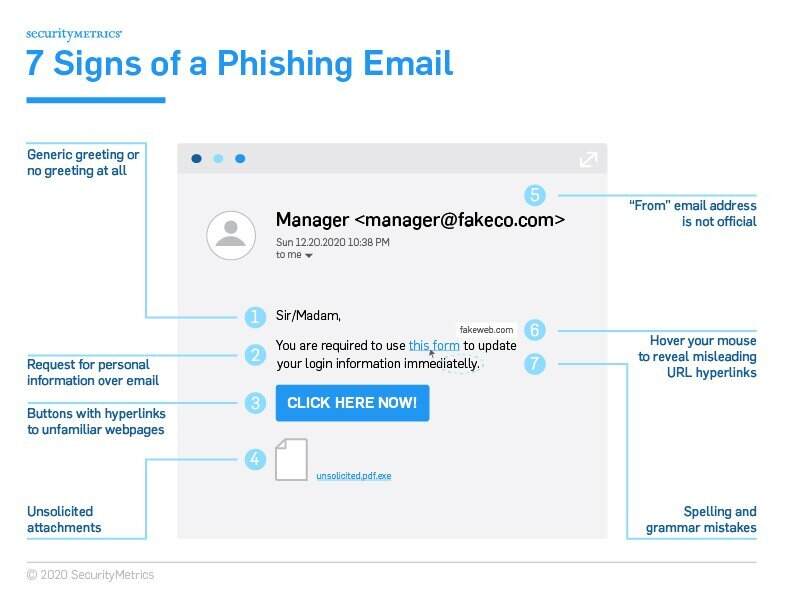
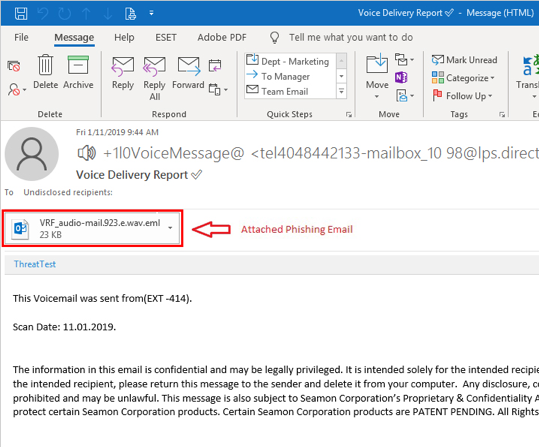
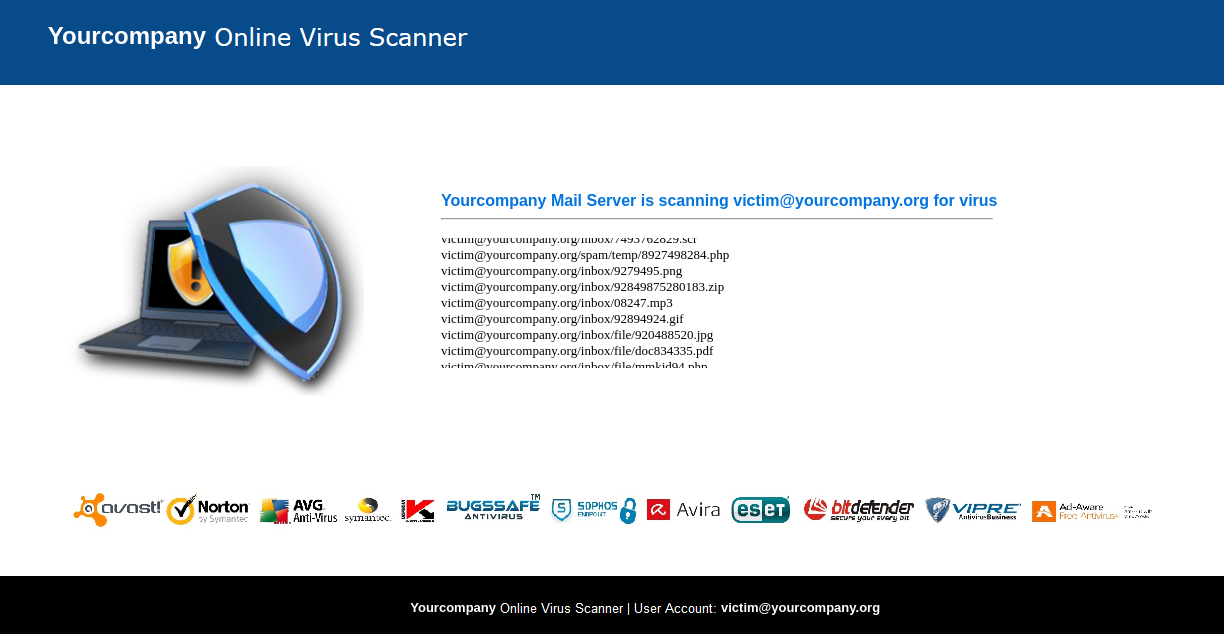
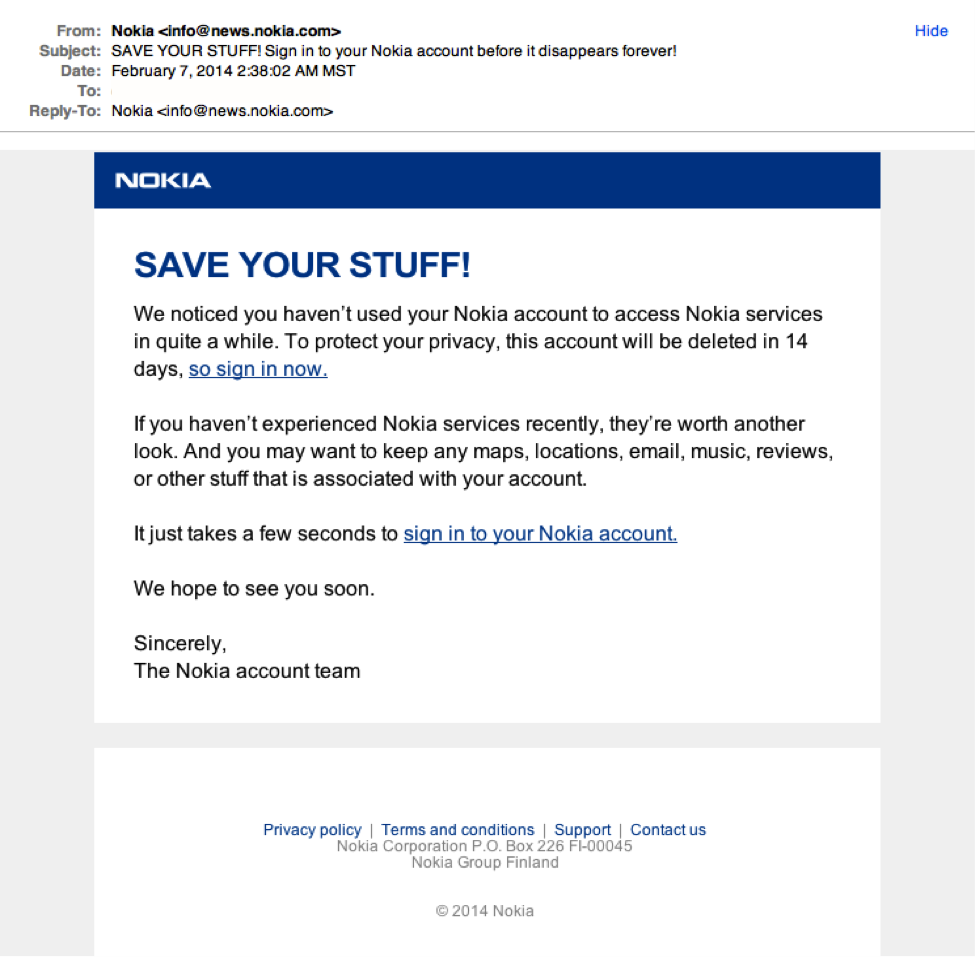
E-mail Phishing Attempts Get Trickier: Fake bounced mail and Fake mail-from- scanner | Disruptive Library Technology Jester
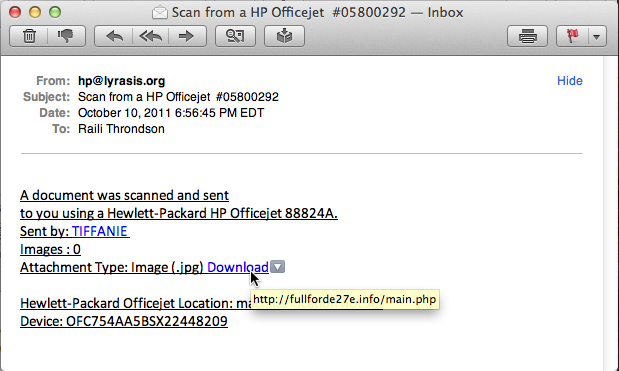
E-mail Phishing Attempts Get Trickier: Fake bounced mail and Fake mail-from- scanner | Disruptive Library Technology Jester