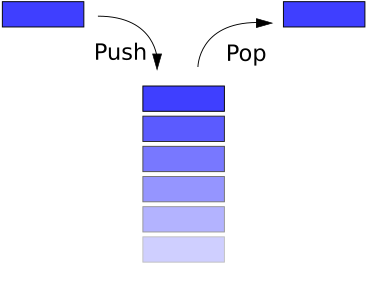
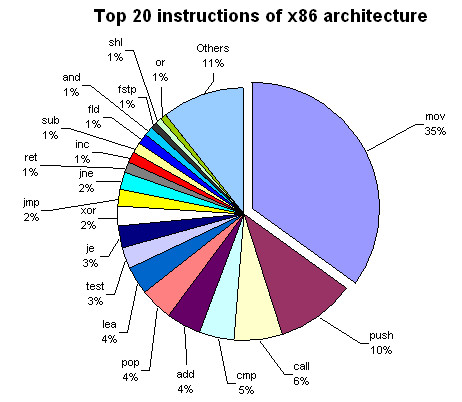
x86 Assembly Language - The Runtime Stack, Push and Pop Operations, and Custom Developed Functions - YouTube
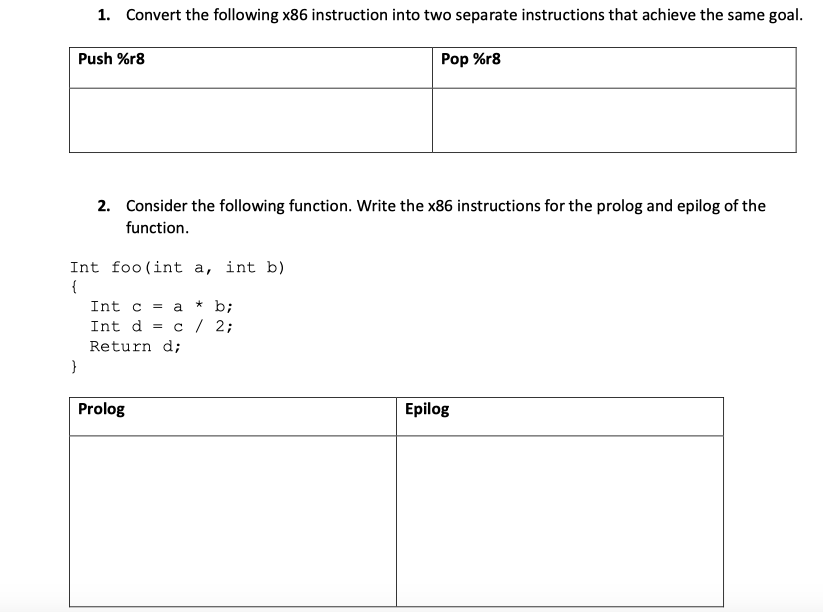
1 Convert Following X86 Instruction Two Separate Instructions Achieve Goal Push 9gr8 Pop 8 Q37224177 - Answer Streak
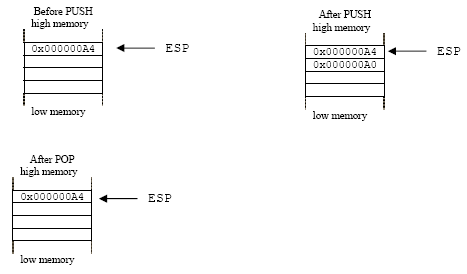
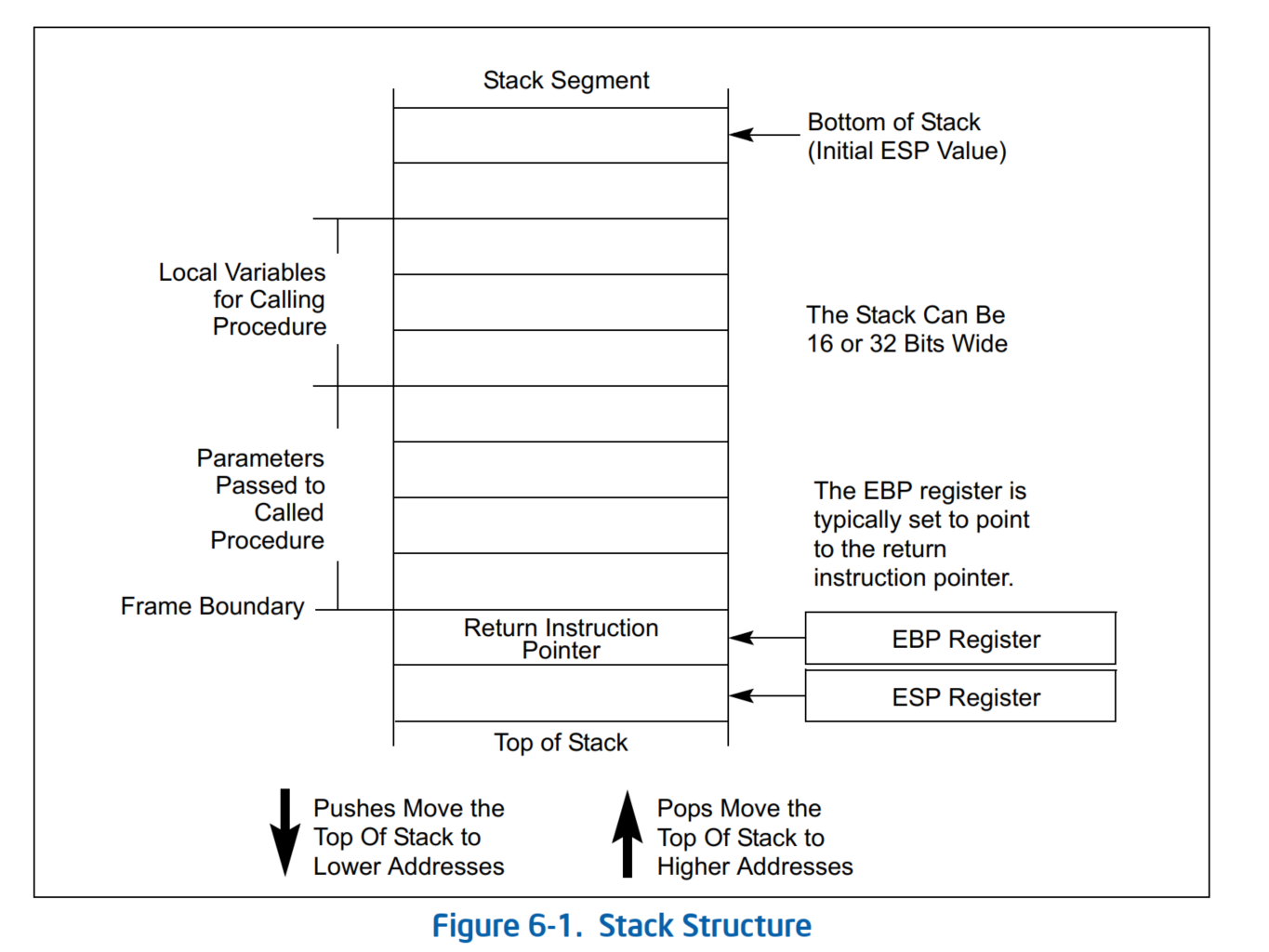
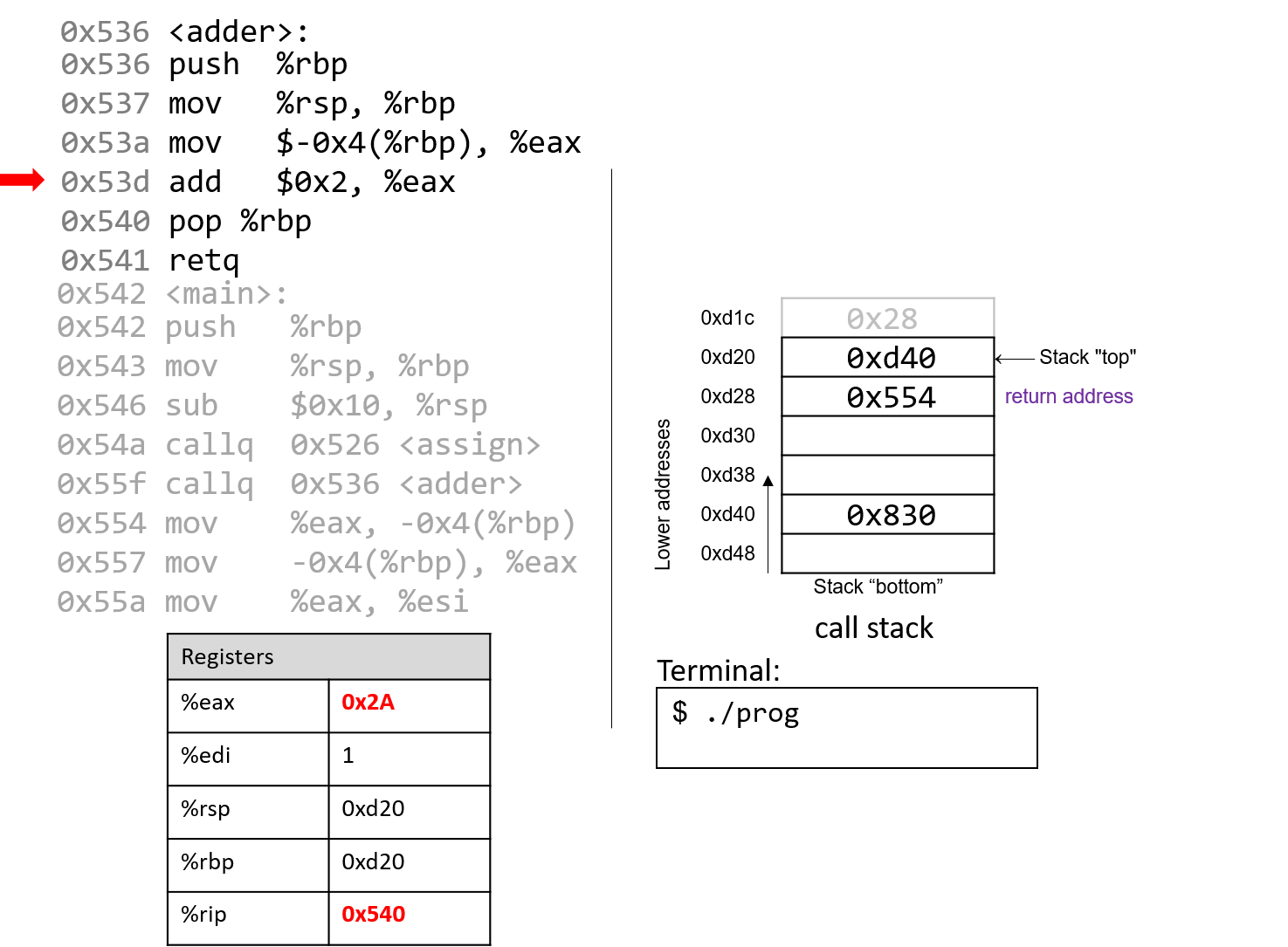
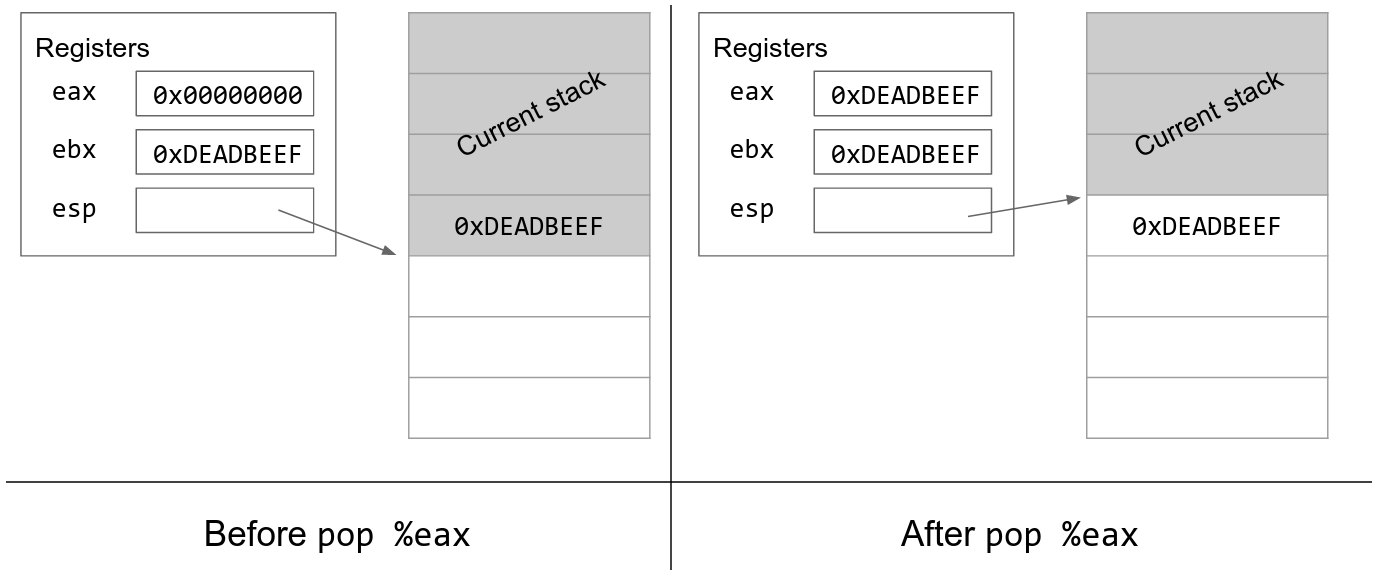
The details of C function stack (and heap) operation when function call is made (caller) and returned (callee) on personal computers