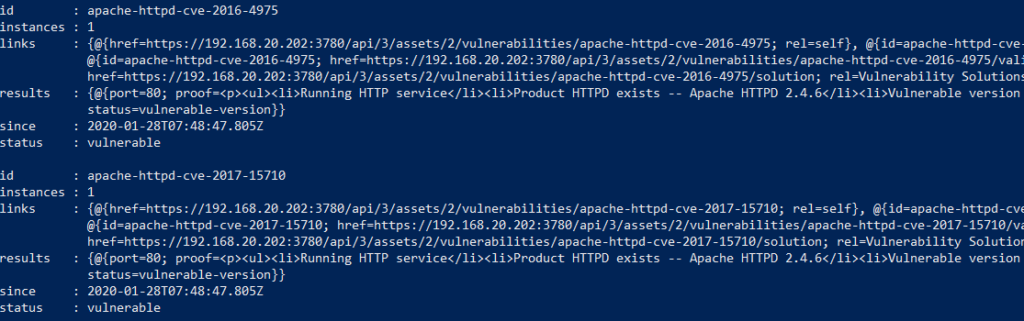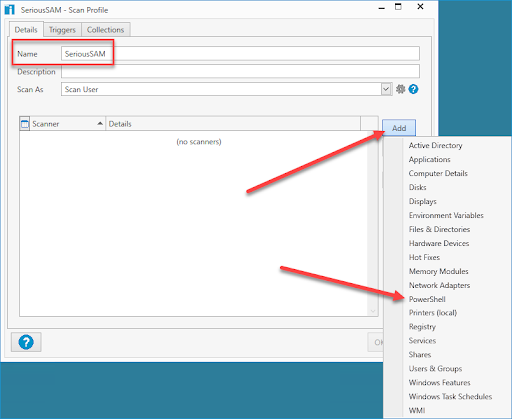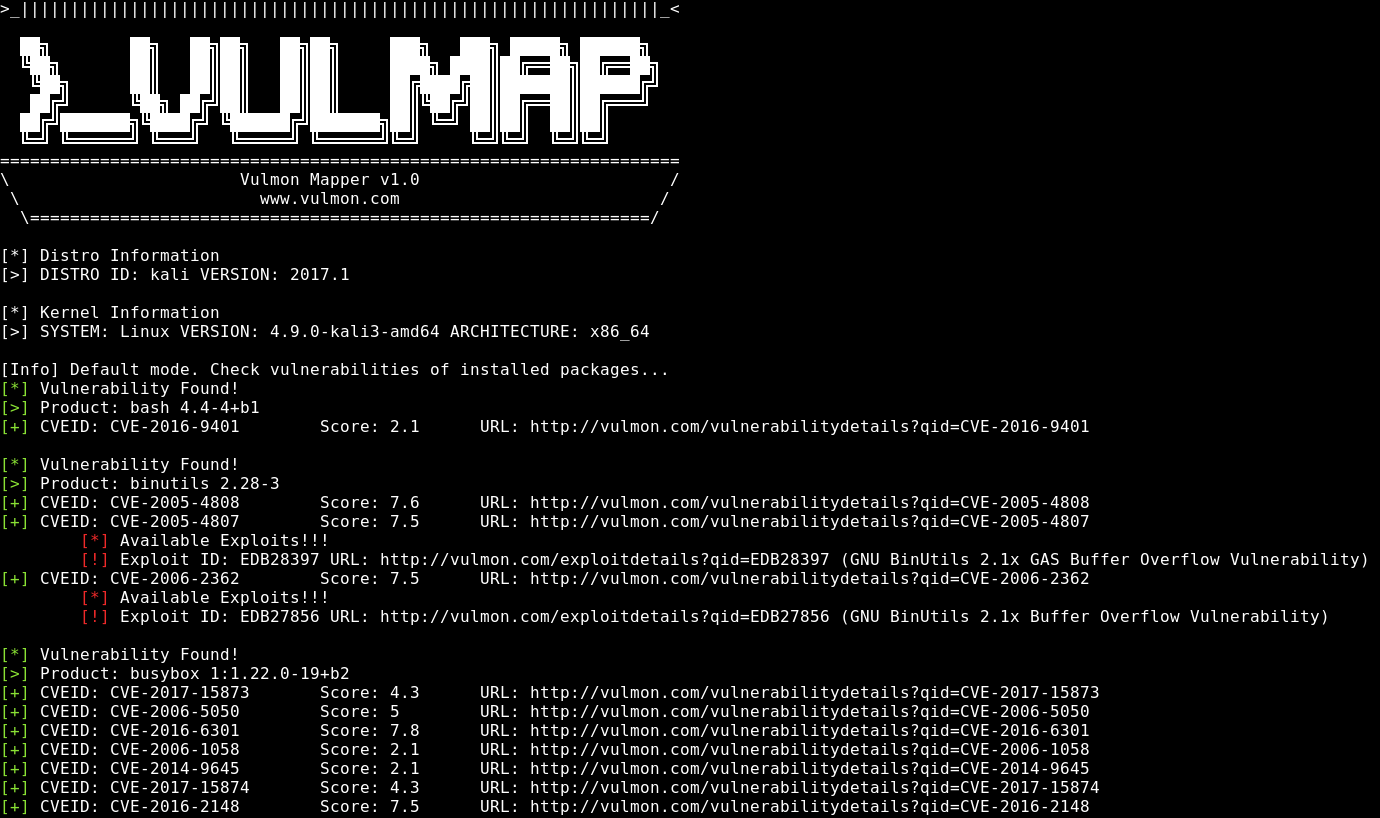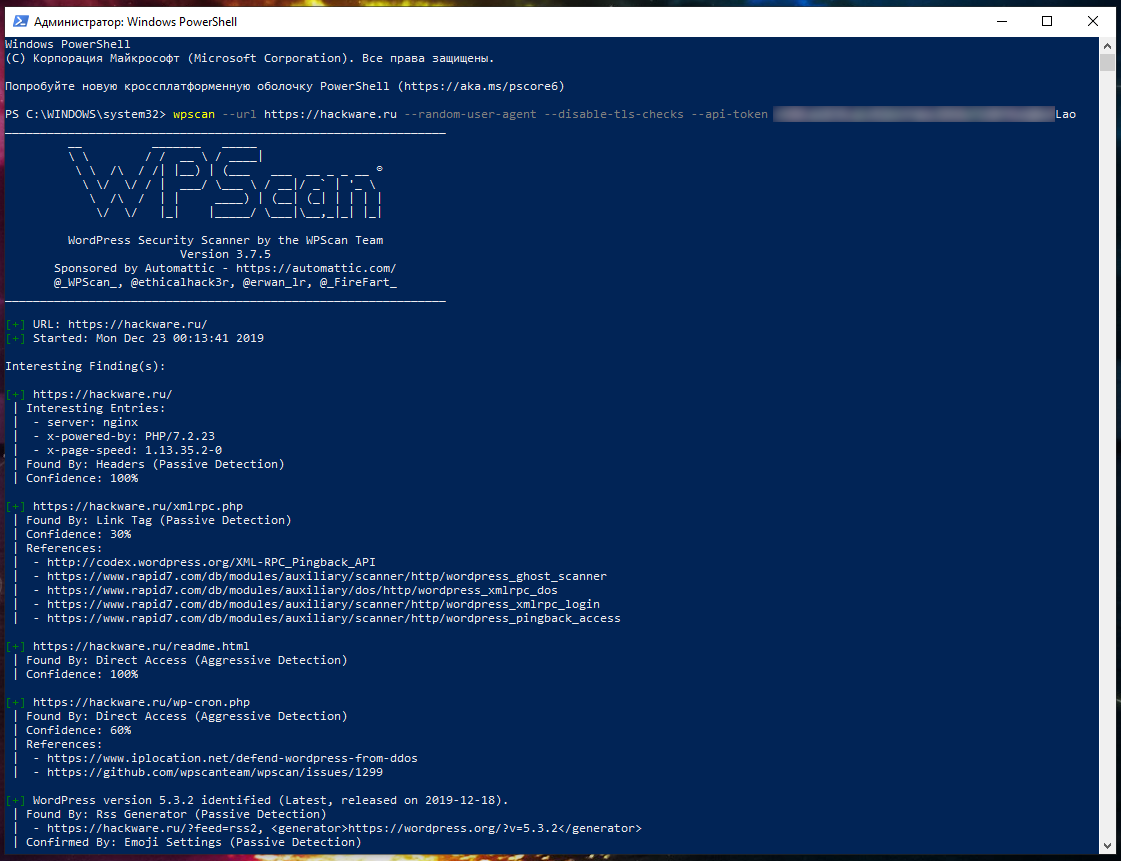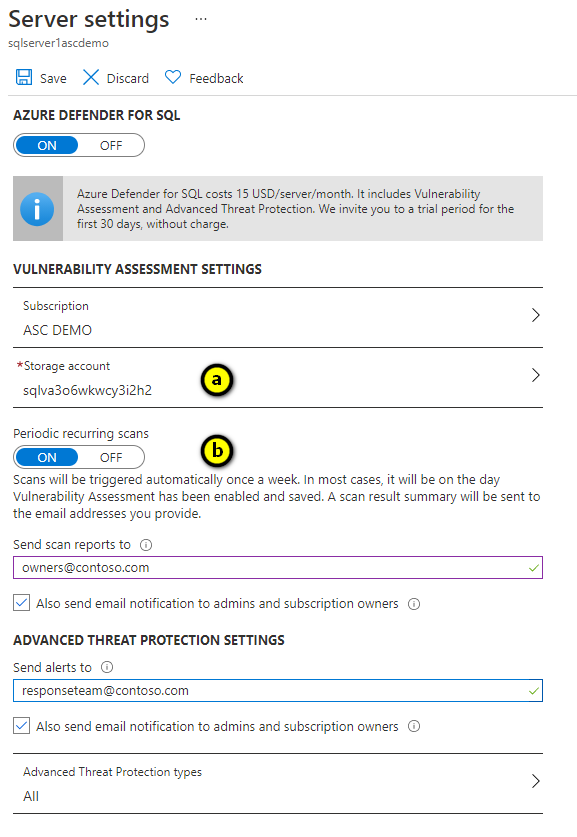
SQL vulnerability assessment - Azure SQL Database & SQL Managed Instance & Azure Synapse Analytics | Microsoft Docs
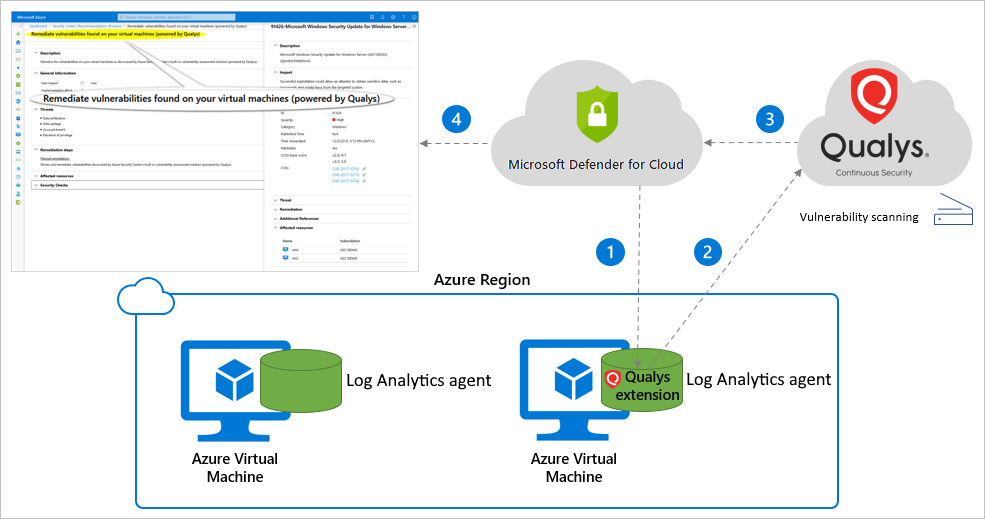
Defender for Cloud's integrated vulnerability assessment solution for Azure, hybrid, and multicloud machines | Microsoft Docs

APT35 exploits Log4j vulnerability to distribute new modular PowerShell toolkit - Check Point Research

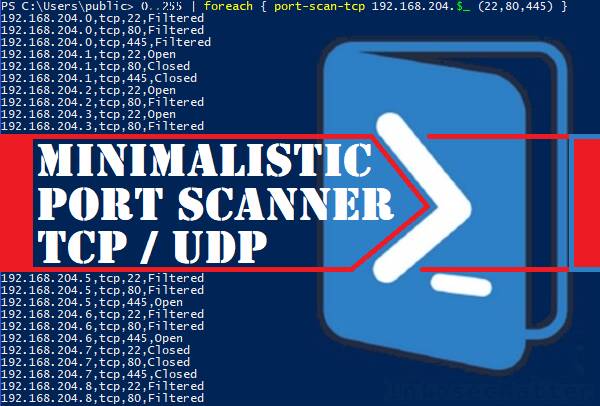
SANS Penetration Testing | Pen Test Poster: "White Board" - PowerShell - Built-in Port Scanner! | SANS Institute

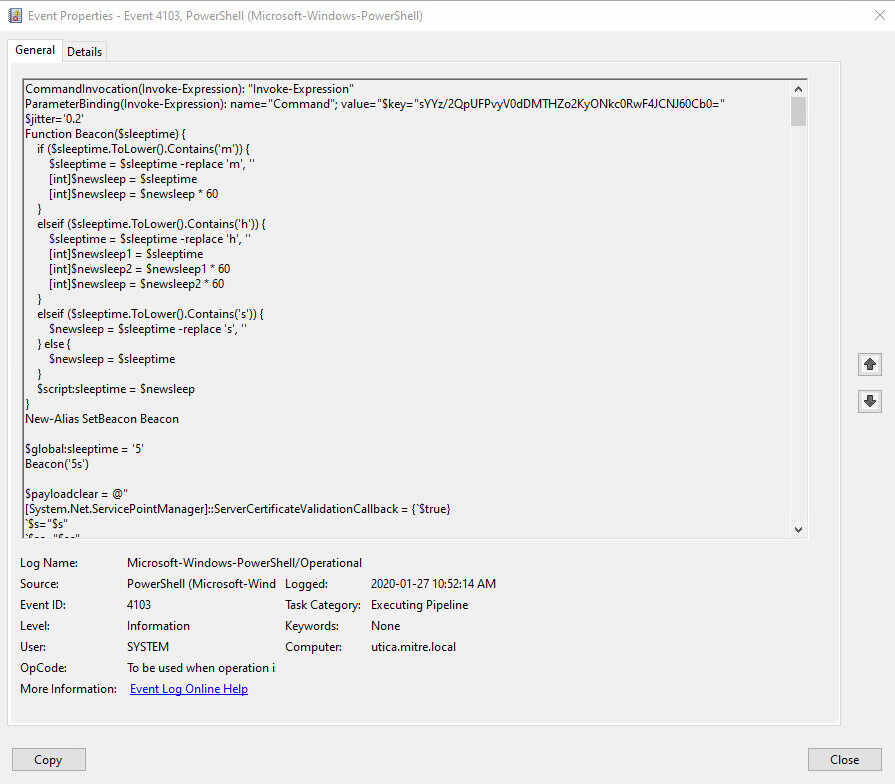
Attack and Defense Around PowerShell Event Logging - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

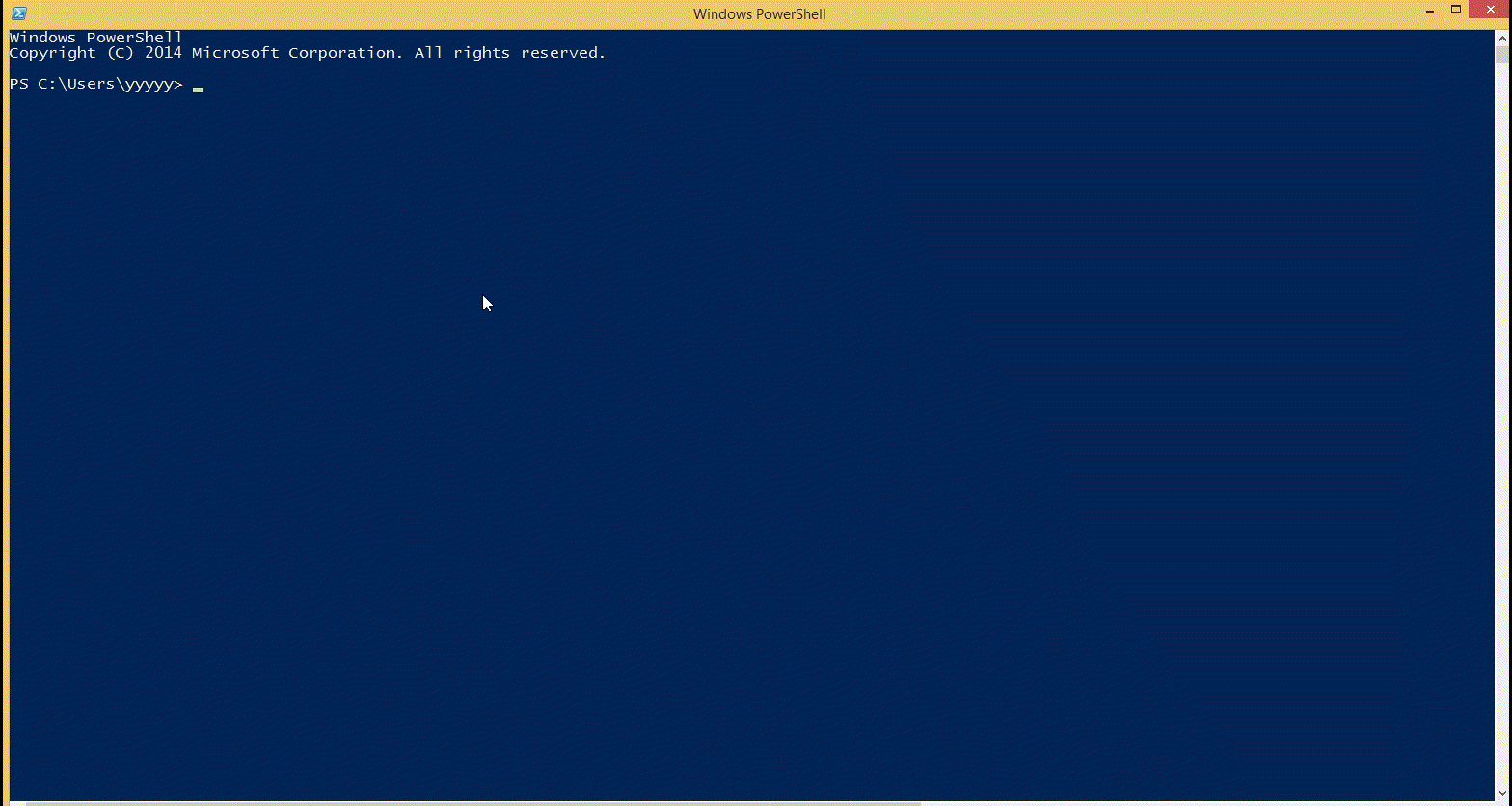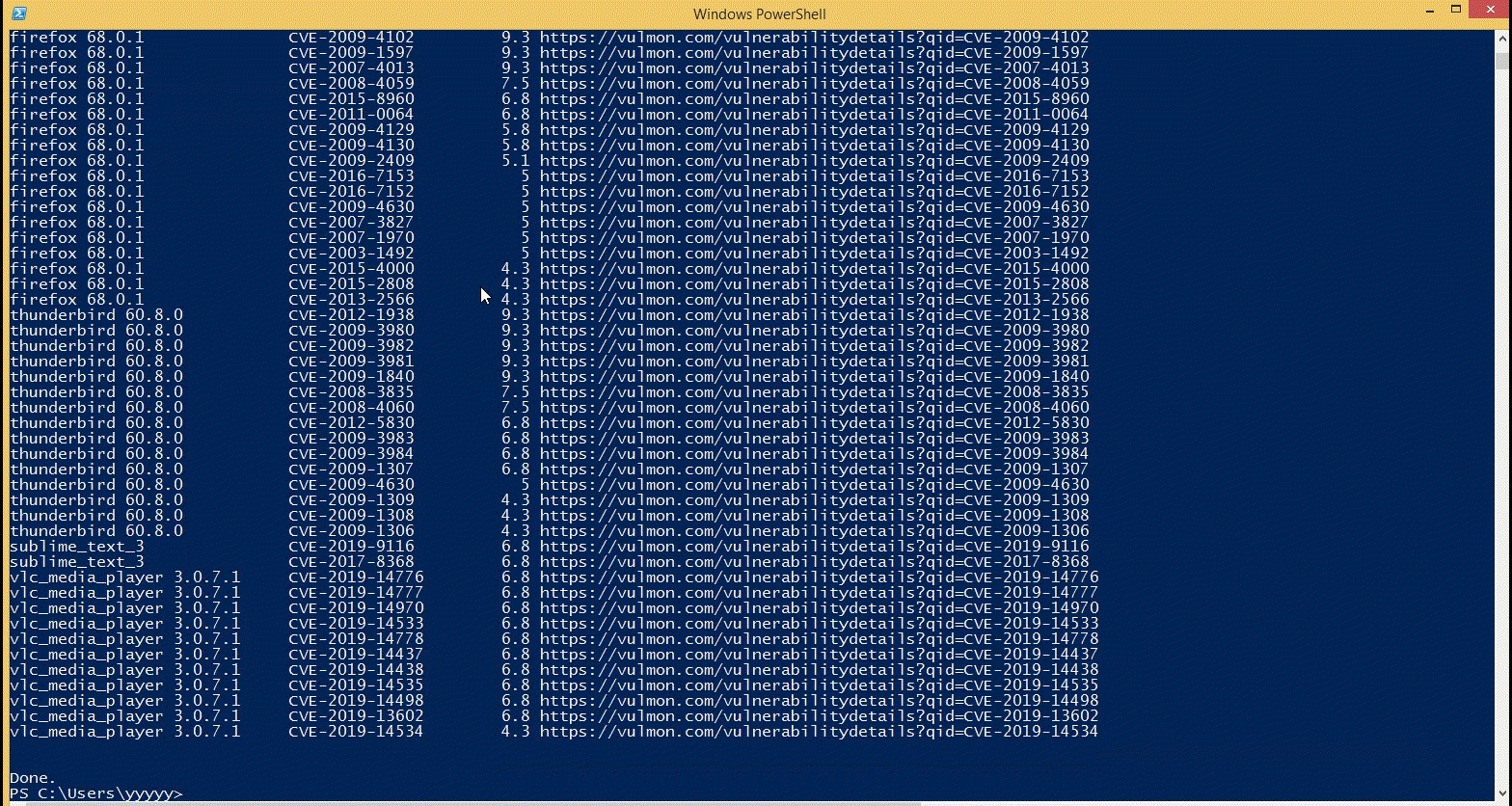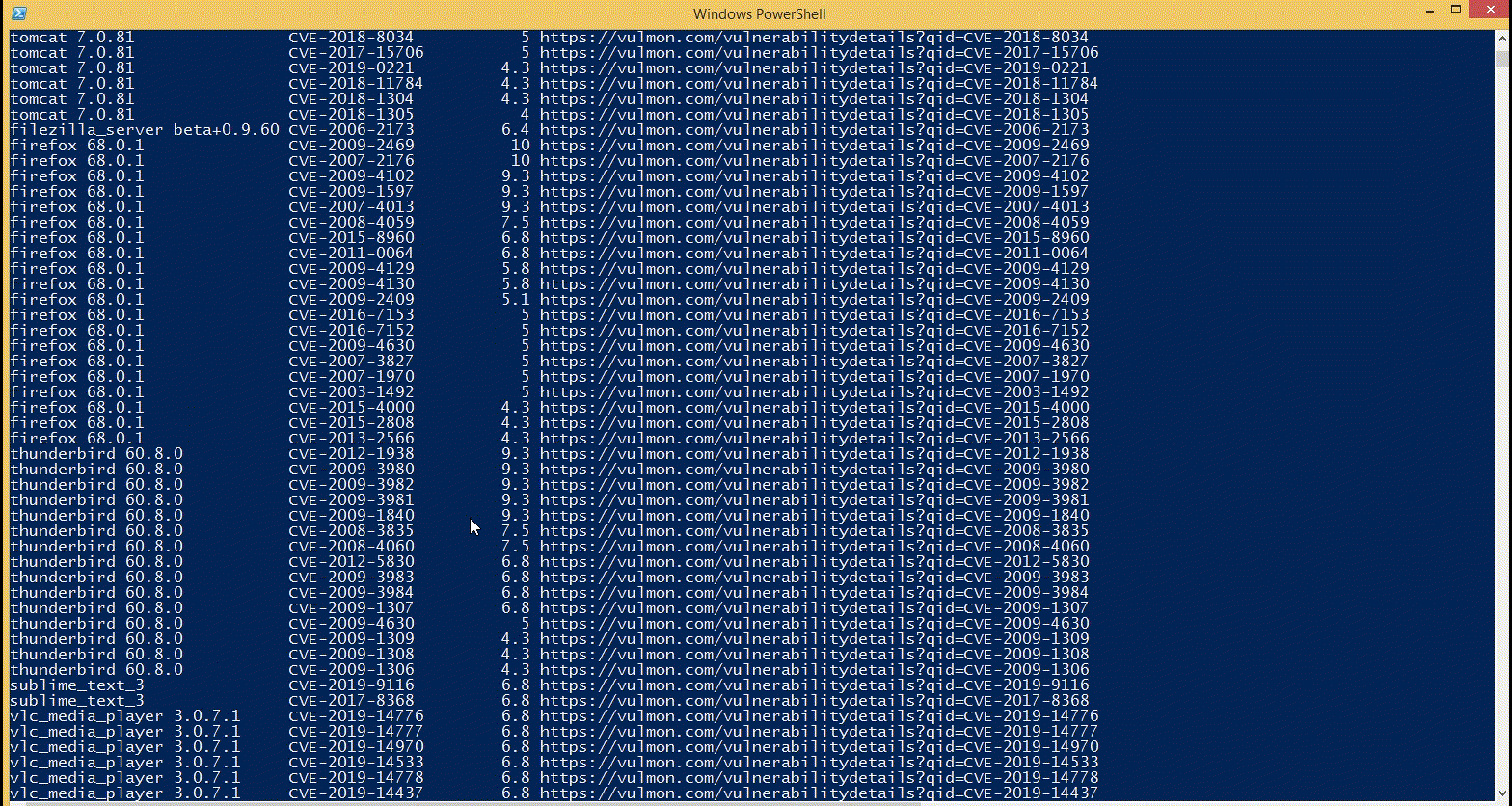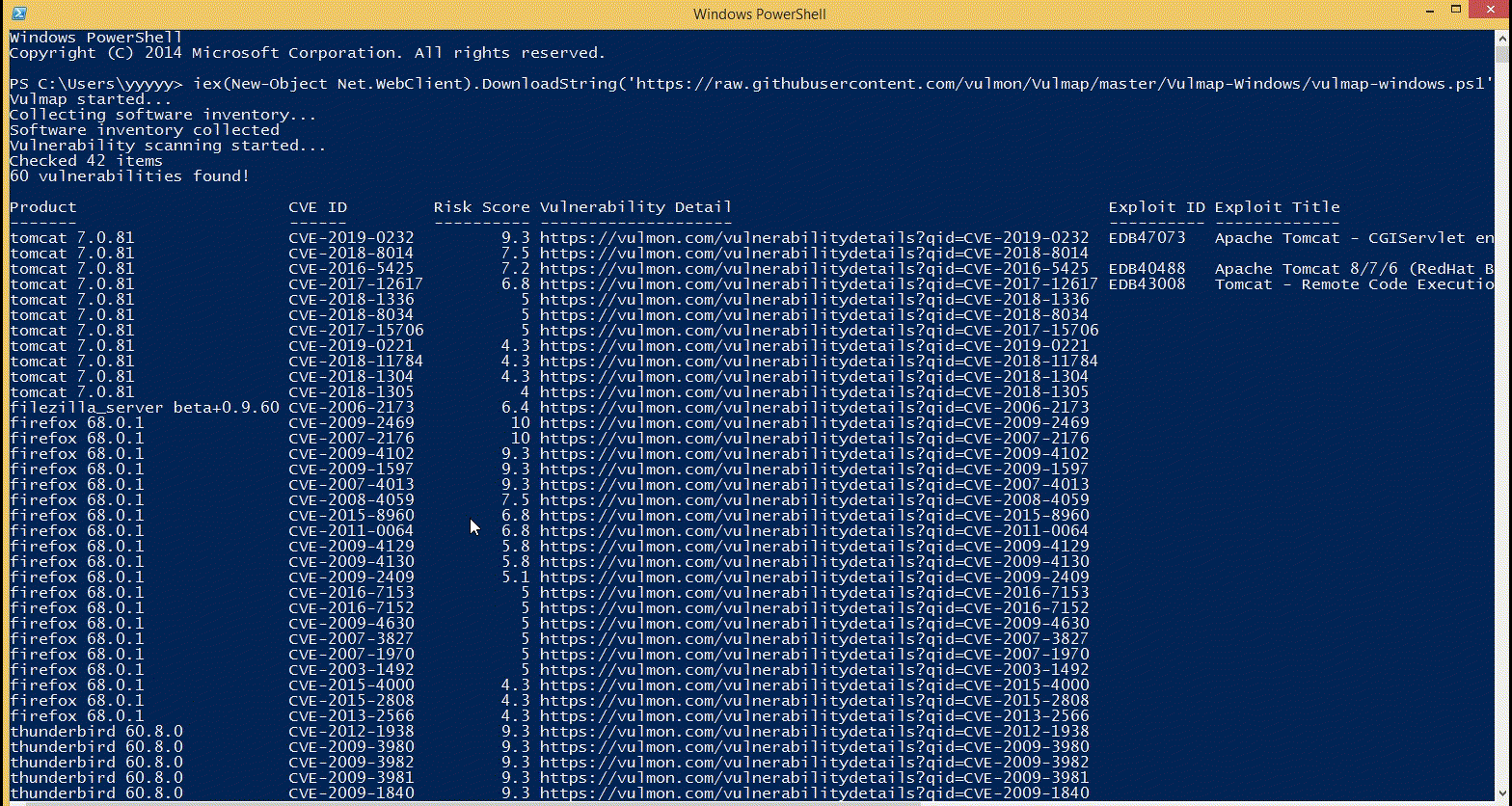
PowerShell "Automation" for larger infrastructure. · Issue #165 · logpresso/CVE-2021-44228-Scanner · GitHub



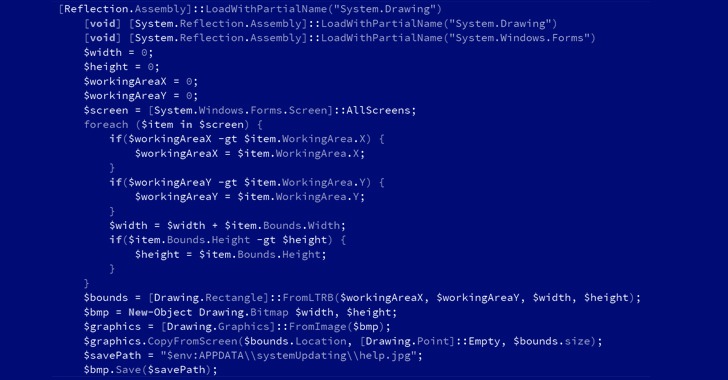

.jpg)