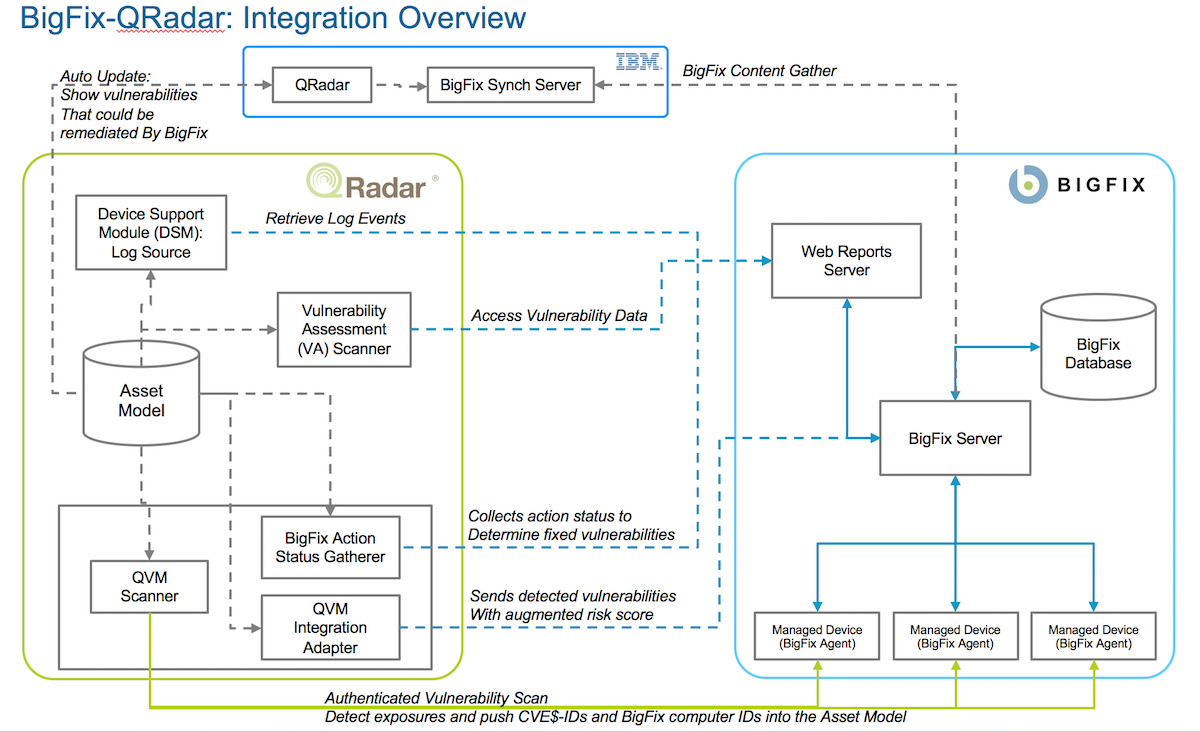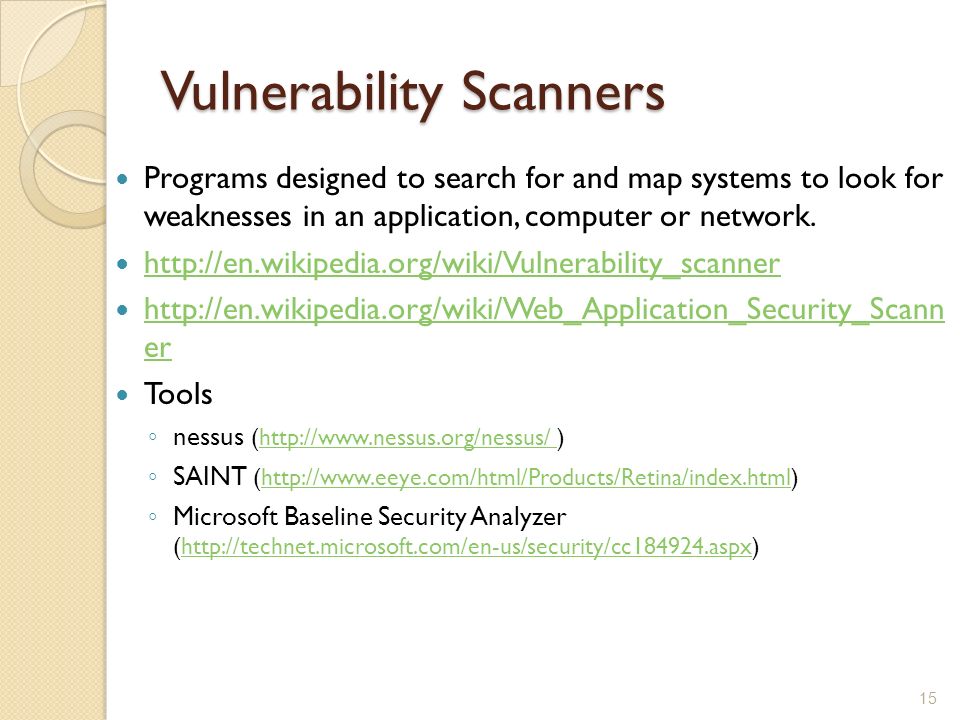
Scanning & Enumeration Lab 3 Once attacker knows who to attack, and knows some of what is there (e.g. DNS servers, mail servers, etc.) the next step is. - ppt download
GitHub - goharbor/harbor-scanner-clair: Use Clair as a plug-in vulnerability scanner in the Harbor registry

Tiki Wiki authentication bypass flaw gives attackers full control of websites, intranets | The Daily Swig

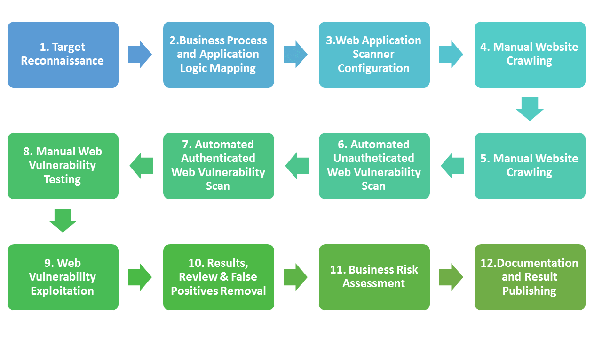




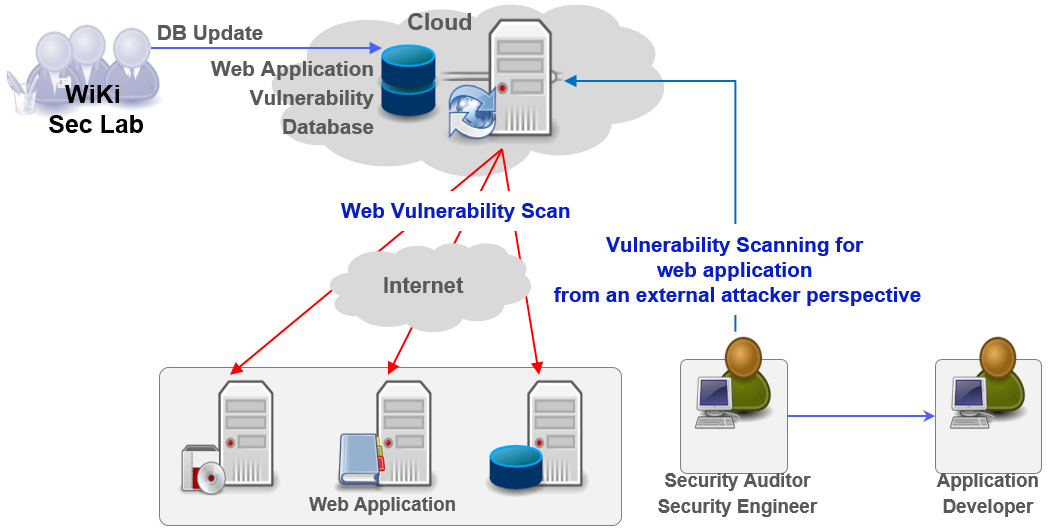






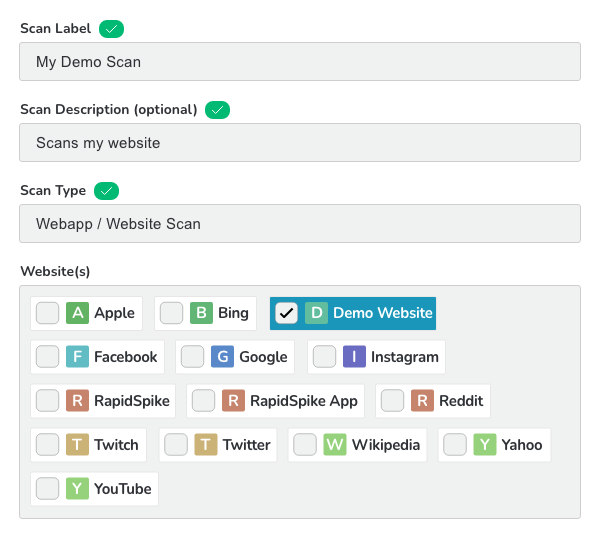
![Different Kali Vulnerability Scanner Tools [Explained] | GoLinuxCloud Different Kali Vulnerability Scanner Tools [Explained] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/Wireshark.png)