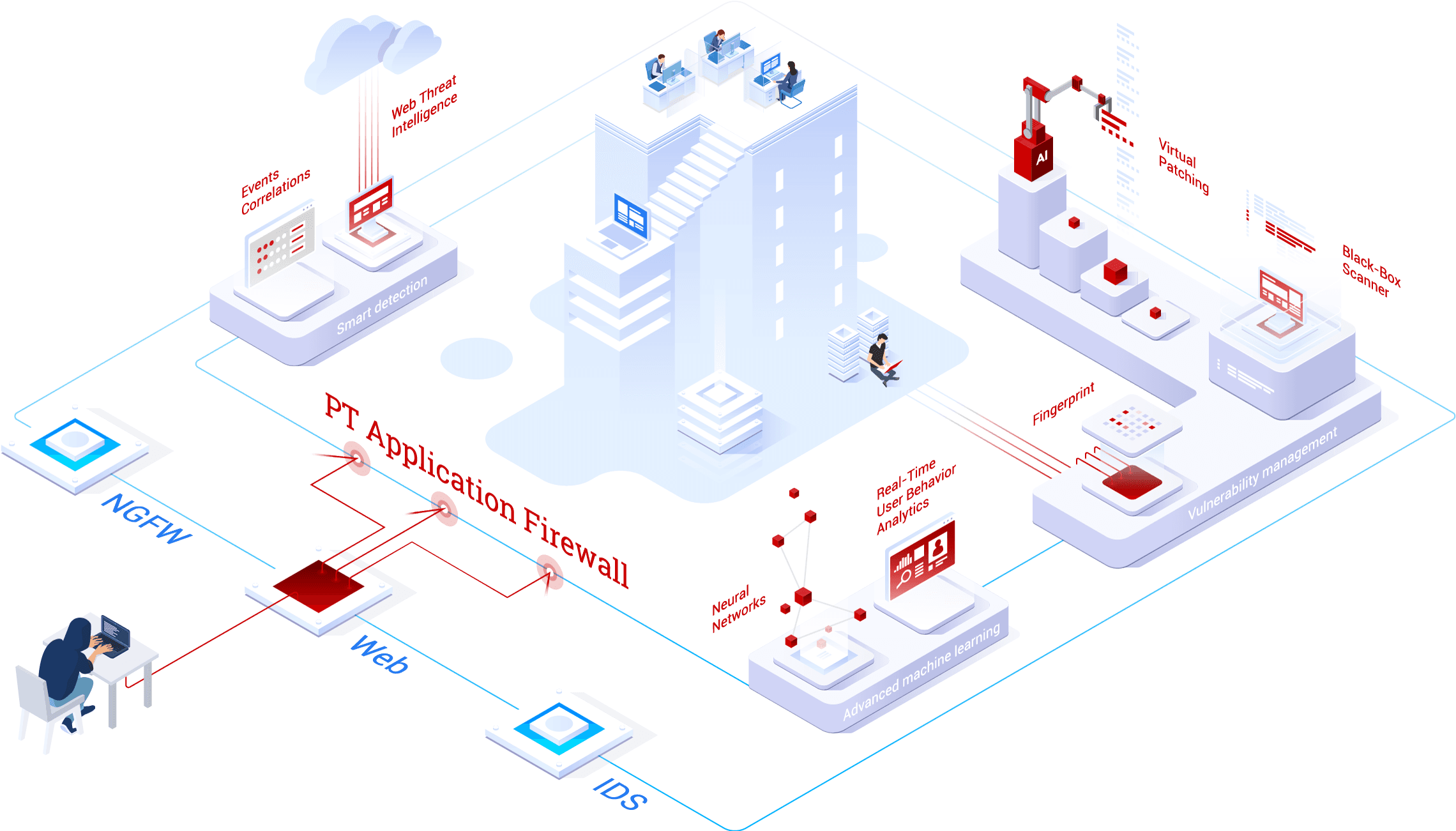
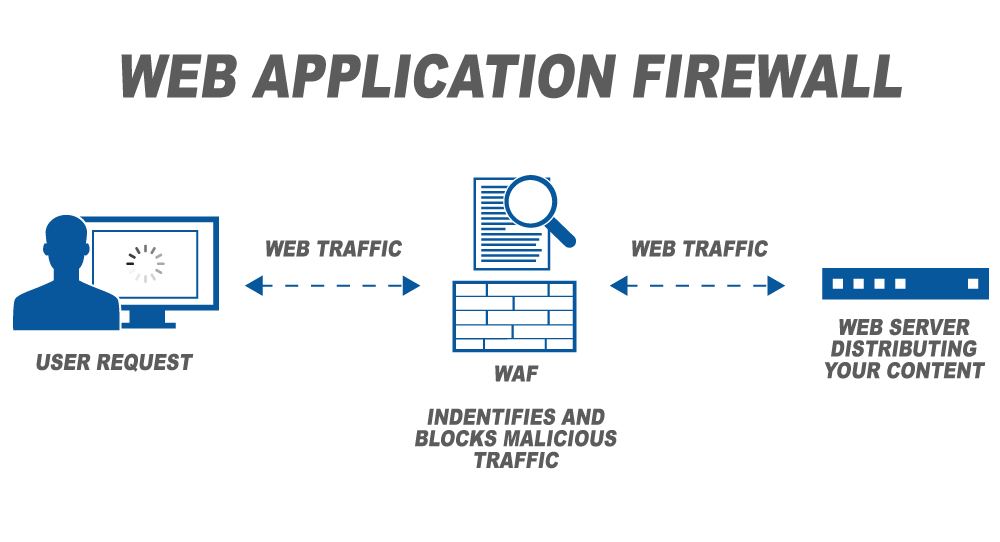
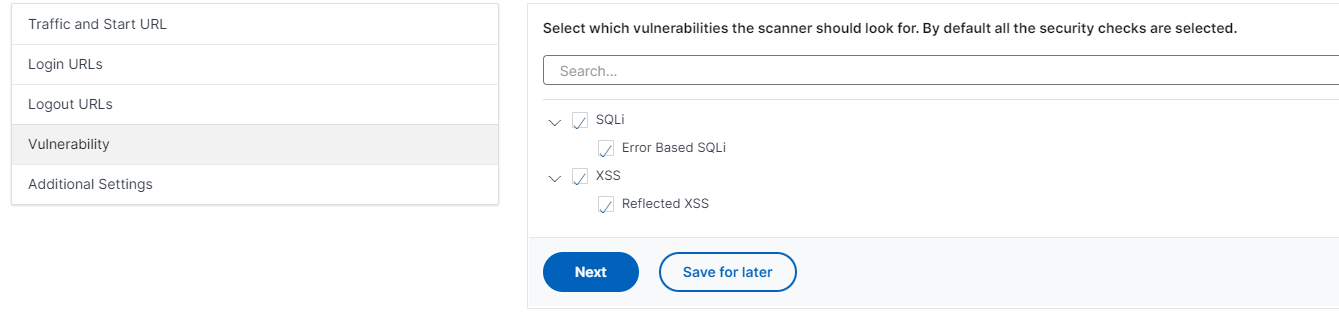
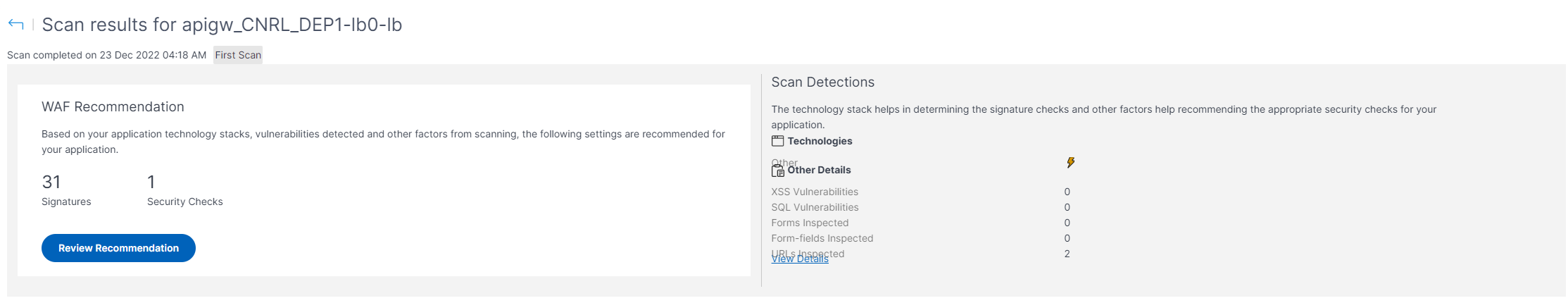
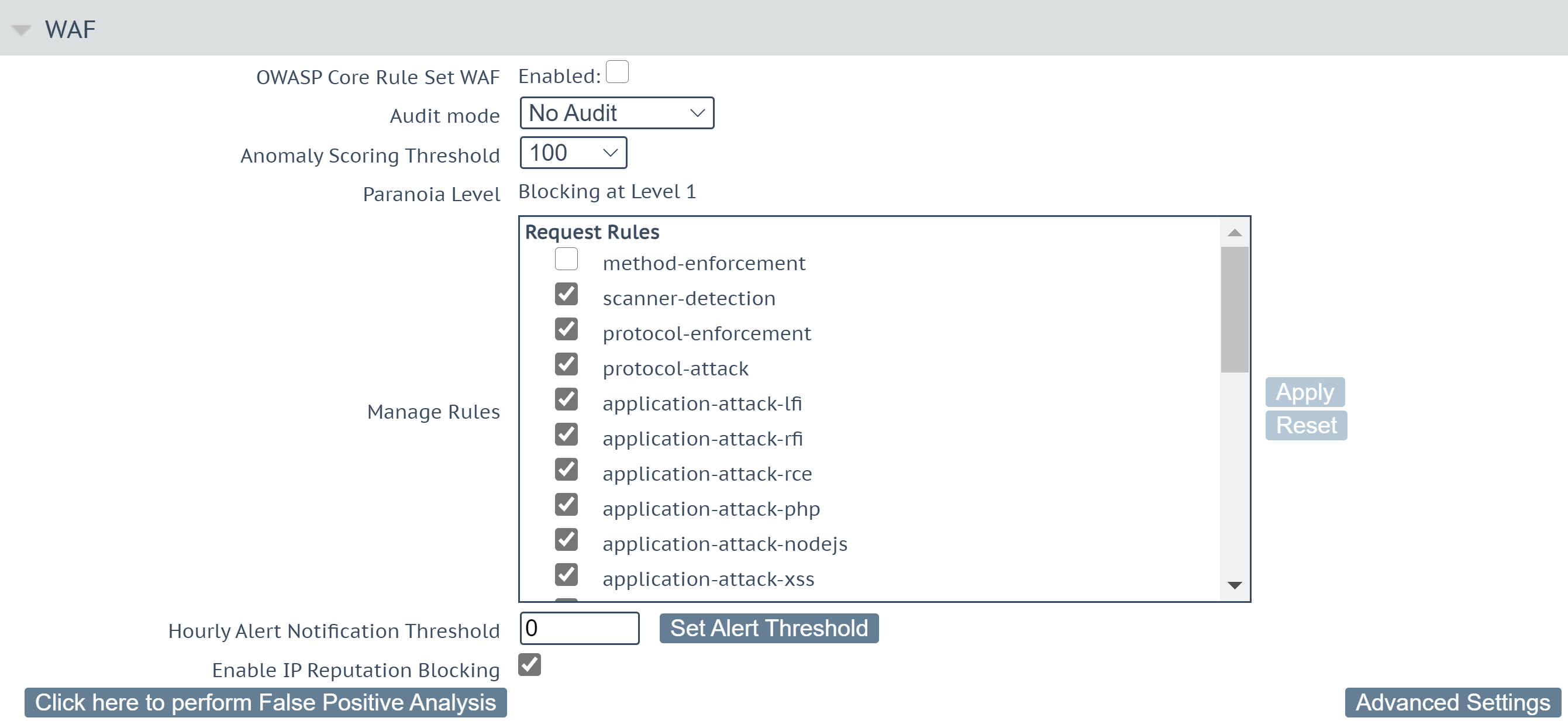
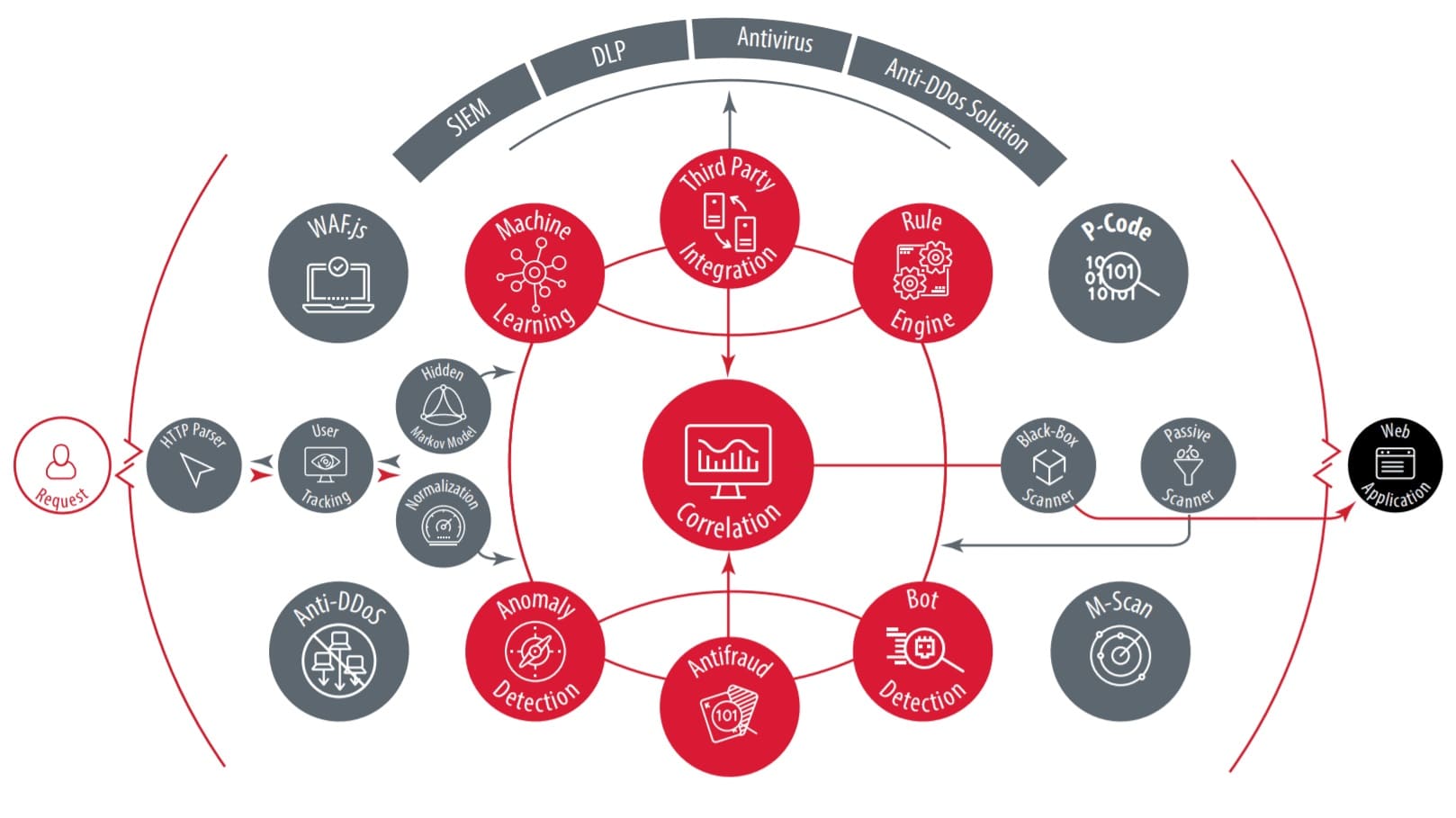
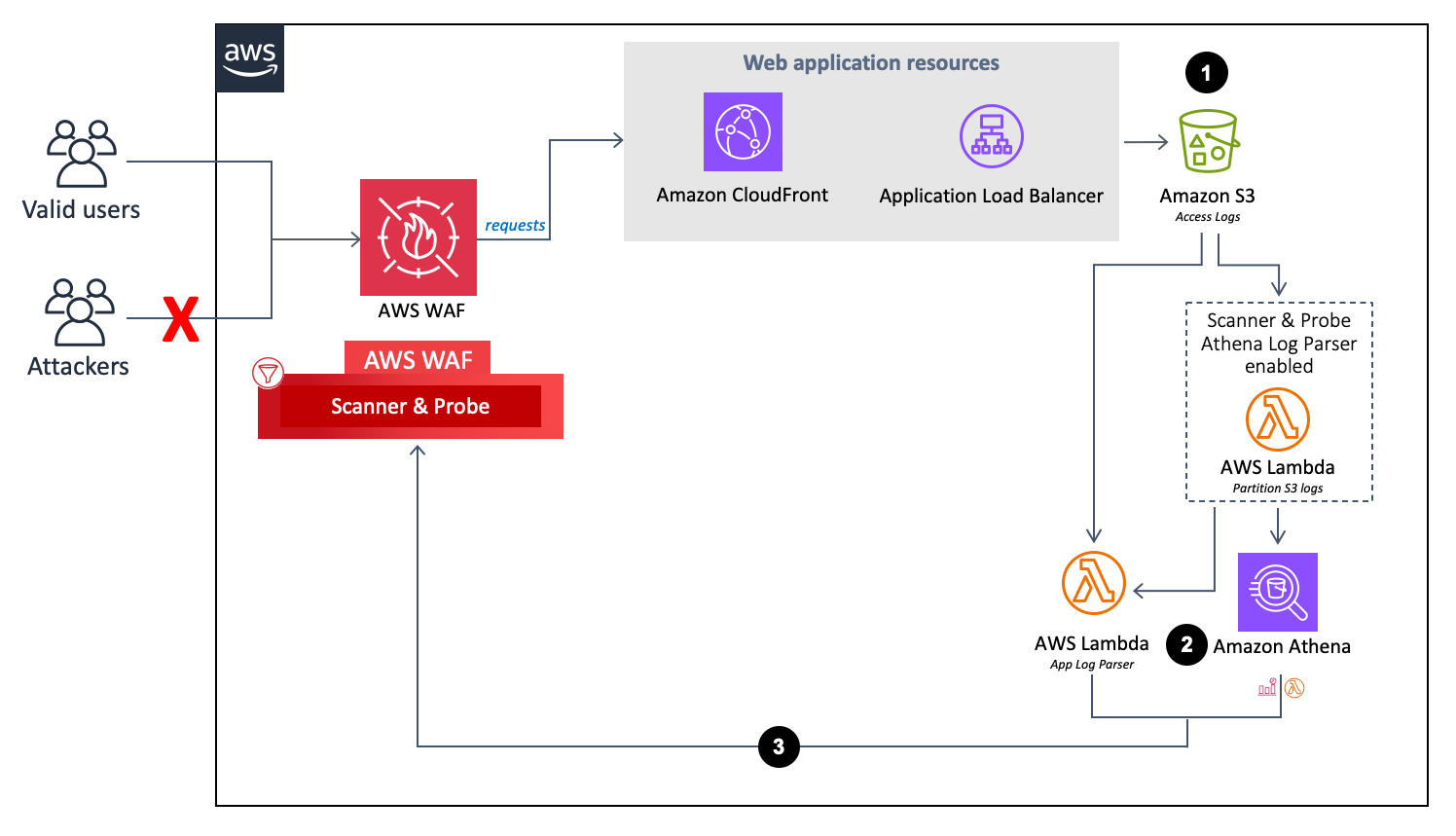
Part 2 - Reconnaissance Playbook: Azure WAF Security Protection and Detection Lab - Microsoft Tech Community
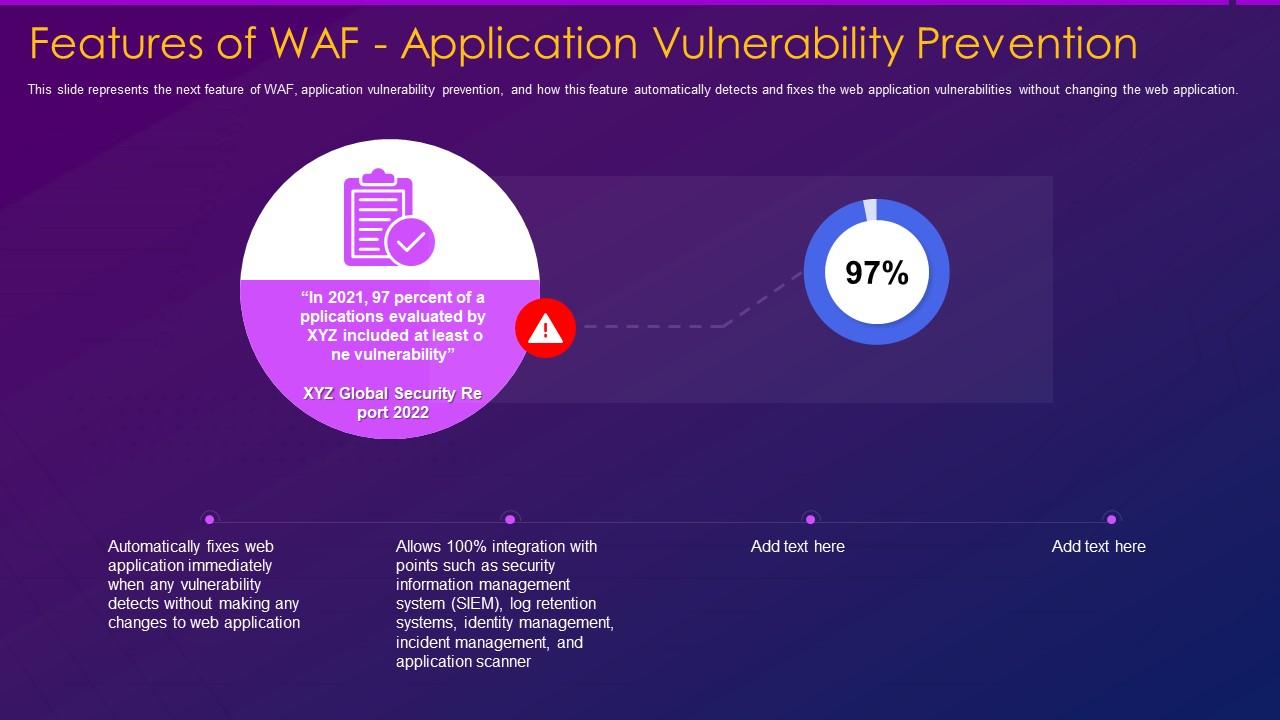
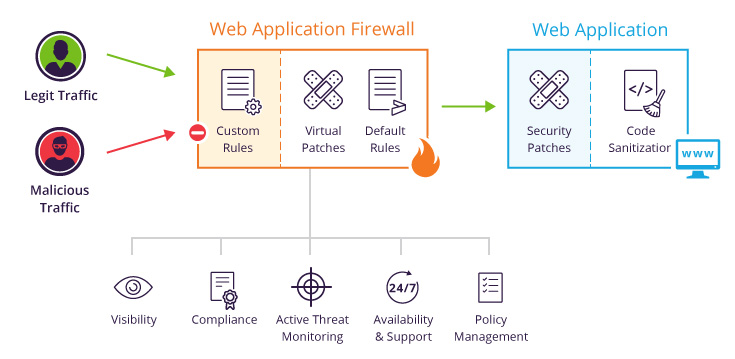
Features Of Waf Application Vulnerability Prevention Web Application Firewall Waf It | Presentation Graphics | Presentation PowerPoint Example | Slide Templates